
Whether you call it personal or privacy information management the subject is growing quickly as a topic of business importance. Threats from massive fines and reputational issues are driving customers to mandate their suppliers show compliance with regulations like GDPR and its counterparts across the world.
Compliance with privacy requirements is complex and on top of broader information security management (i.e. for other information assets like commercial contracts, IPR and financial data) can be a real challenge. We can help you with various levels of privacy compliance and will also help you work out what level of privacy information management system (PIMS) you might need and why.
Whether your organisation is a controller or a processor, or both, it needs to protect the personal data of individuals. Personal data is any information that relates to an identified or identifiable individual. It can cover anything from a name and address, to a record of purchases made, to confidential medical records.
Personal data protection regulations and methods are developing fast. And there are different ways of describing the data you’re protecting. For example:
To keep things simple, we usually call it personal data.
Third parties also differ in their naming convention for management systems around it too, for example:
At least both of those specific terms shorten to PIMS, so that’s what we call it!
There are many benefits associated with a PIMS and it should be something that helps grow value for the organisation as well as help manage threats. Benefits include:
Book a tailored hands-on session based on your needs and goals.
There are are a growing number of privacy frameworks which does not help the simplification goal and they broadly break down into 2 types:
We’ve turned the complexity into a simplified approach towards 5 levels of maturity.
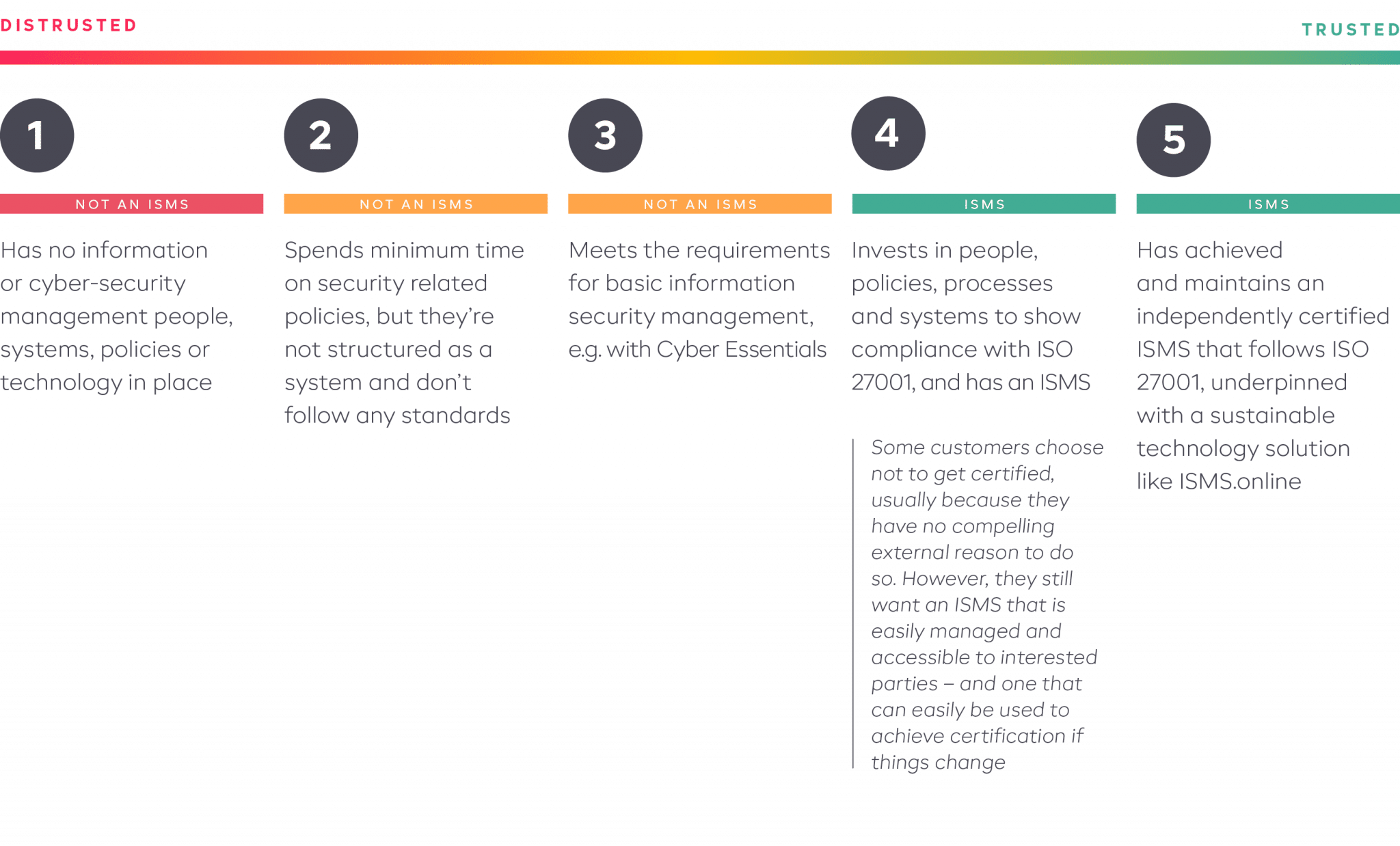
It goes without saying that levels 1 and 2 are unlikely to demonstrate any form of protection or value for the organisation and its stakeholders. We can help you from Level 3–5.
IDEAL FOR: Starting out your privacy management/data protection compliance journey in a recognised, structured and effective way.
Data Protection – Specification for a personal information management system
IDEAL FOR: Implementing a regulation based PIMS where there is no need for an Information Security Management System (ISMS) i.e. you don’t need or have any intention of doing ISO 27001.
Security techniques – Extension to ISO/IEC 27001 and ISO/IEC 27002 for privacy information management – Requirements and guidelines
IDEAL FOR: Implementing an information security based PIMS If you have an Information Security Management System (ISMS) or are willing to get one.
Data Protection – Specification for a personal information management system
IDEAL FOR: Implementing a regulation based PIMS where there is no need for an Information Security Management System (ISMS) i.e. you don’t need or have any intention of doing ISO 27001.
Security techniques – Extension to ISO/IEC 27001 and ISO/IEC 27002 for privacy information management – Requirements and guidelines
IDEAL FOR: Implementing an information security based PIMS If you have an Information Security Management System (ISMS) or are willing to get one.
We’ve preconfigured various PIMS solutions to meet your needs with the aim of simplification and ease of completion at their heart. As with all the ISMS.online features they are fit for use whether you are a newcomer, improver or an expert and the PIMS takes advantage of our tried and tested ISMS functionality.
In addition you can also:
We make data mapping a simple task. It’s easy to record and review it all, adding your organisation’s details to our pre-configured dynamic Records of Processing Activity tool.
You’ll need to show how well you manage Subject Access Requests. Our secure SAR space keeps it all in one place, supporting it with automated reporting and insight.
We’ve created a built-in risk bank and a range of other practical tools that’ll help with every part of the risk assessment and management process.
It’s easy to set up and run different kinds of privacy assessment, from data protection impact assessments to regulatory or compliance readiness ones.
You’ll be ready when the worst happens. We make it easy to plan and communicate your breach workflow, and document and learn from each and every incident.
Our workspace makes collaboration easy and simplifies progress monitoring, with a simple approval process and automated reviews built in as standard.
We can help you show that you’re in control of your supply chain, covering everything from contracts and contacts to relationship and performance management and monitoring.
Your staff need to be right at the heart of your GDPR solution. Our optional comms and engagement tools can help you bring them on board and keep them compliant.

Easily collaborate, create and show you are on top of your documentation at all times
Find out more
Effortlessly address threats & opportunities and dynamically report on performance
Find out more
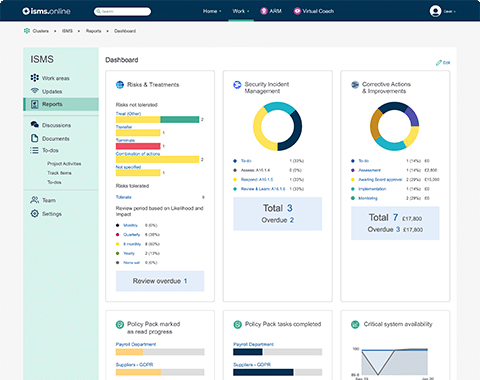
Make better decisions and show you are in control with dashboards, KPIs and related reporting
Find out more
Make light work of corrective actions, improvements, audits and management reviews
Find out more
Shine a light on critical relationships and elegantly link areas such as assets, risks, controls and suppliers
Find out moreSelect assets from the Asset Bank and create your Asset Inventory with ease
Find out more
Out of the box integrations with your other key business systems to simplify your compliance
Find out more
Neatly add in other areas of compliance affecting your organisation to achieve even more
Find out more
Engage staff, suppliers and others with dynamic end-to-end compliance at all times
Find out more
Manage due diligence, contracts, contacts and relationships over their lifecycle
Find out more
Visually map and manage interested parties to ensure their needs are clearly addressed
Find out more
Strong privacy by design and security controls to match your needs & expectations
Find out more100% of our users achieve ISO 27001 certification first time