What is ISO 27002?
ISO/IEC 27002:2022 is an information security standard published by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). ISO 27002 has a close association with ISO 27001. Broadly speaking, it gives guidance on implementing an ISO 27001 ISMS.
ISO/IEC 27002 provides a reference set of information security, cyber security and privacy protection controls, including implementation guidance based on internationally recognised best practices.
While ISO 27002 is not a certifiable standard by itself, compliance with its information security, physical security, cyber security and privacy management guidelines brings your organisation one step closer to meeting ISO 27001 certification requirements.
Why is ISO 27002 important?
If your organisation collects, uses, or processes data, there will always be information security risks and threats to watch out for.
To guard against these risks, you should have an Information Security Management System (ISMS) to ensure the confidentiality, availability, and integrity of all information and information assets.
The main challenge facing businesses new to the information security management scene is its broad scope. Implementing and maintaining an ISMS covers such a broad spectrum that most managers don’t know where to begin.
If this sounds like you or if you are just looking to stay on top of your information security, then a great starting point is implementing the controls suggested in ISO/IEC 27002.
Make it simpler with ISMS.online
The ISMS.online platform offers step-by-step guidance taking from setting up your ISMS all the way to certification, with a 100% success rate.
Book a demo today to see how we can help your business.
What are the benefits?
By implementing information security controls found in ISO 27002, organisations can rest assured that their information assets are protected by internationally recognised and approved best practices.
Organisations of all sizes and levels of security maturity can reap the following benefits from adherence to the ISO 27002 code of practice:
- It provides a working framework for the resolution of information security, cyber security, physical security and information privacy issues.
- Clients and business partners will be more confident and will take a positive view of an organisation that implements the recommended standards and information security controls.
- Since the policies and procedures provided align with internationally recognised security requirements, cooperation with international partners is more straightforward.
- Compliance with the standard helps develop an organisation’s best practices which will increase overall productivity.
- It provides a defined implementation, management, maintenance and evaluation of information security management systems.
- An ISO-compliant organisation will have an advantage in contract negotiations and participation in global business opportunities.
- By complying with ISO 27002 information security controls, one can benefit from lower insurance premiums from providers.
Implementation guidance for compliance with the ISO 27001 standard is widely referenced within the ISO 27000 family of standards, including ISO 27701. ISO 27002 information security controls can be mapped against similar standards, e.g. NIST, SOC2, CIS, TISAX® and many more.
The ISO 27002:2022 revision explained
ISO/IEC 27002 has been revised to update the information security controls so that they reflect developments and current information security practices in various sectors of businesses and governments.
The new ISO 27002 2022 revision was published on the 15th of February 2022. Many standards and security frameworks are related to or make use of ISO 27002:2013’s information security controls and so this new revision will also impact them.
ISO 27002:2013 scope
ISO 27002:2013 is/was a code of practice for an information security management system (ISMS) and delves into a much higher level of detail than the Annex A Controls of ISO 27001, containing security techniques, control objectives, security requirements, access control, information security risk treatment controls, personal and proprietary information controls as well as generic information security controls.
The primary purpose of ISO 27002:2013 was to provide comprehensive information security techniques and asset management controls for any organisation that either needed a new information security management program or wanted to improve their existing information security policies and practices.
What has changed in ISO 27002:2022?
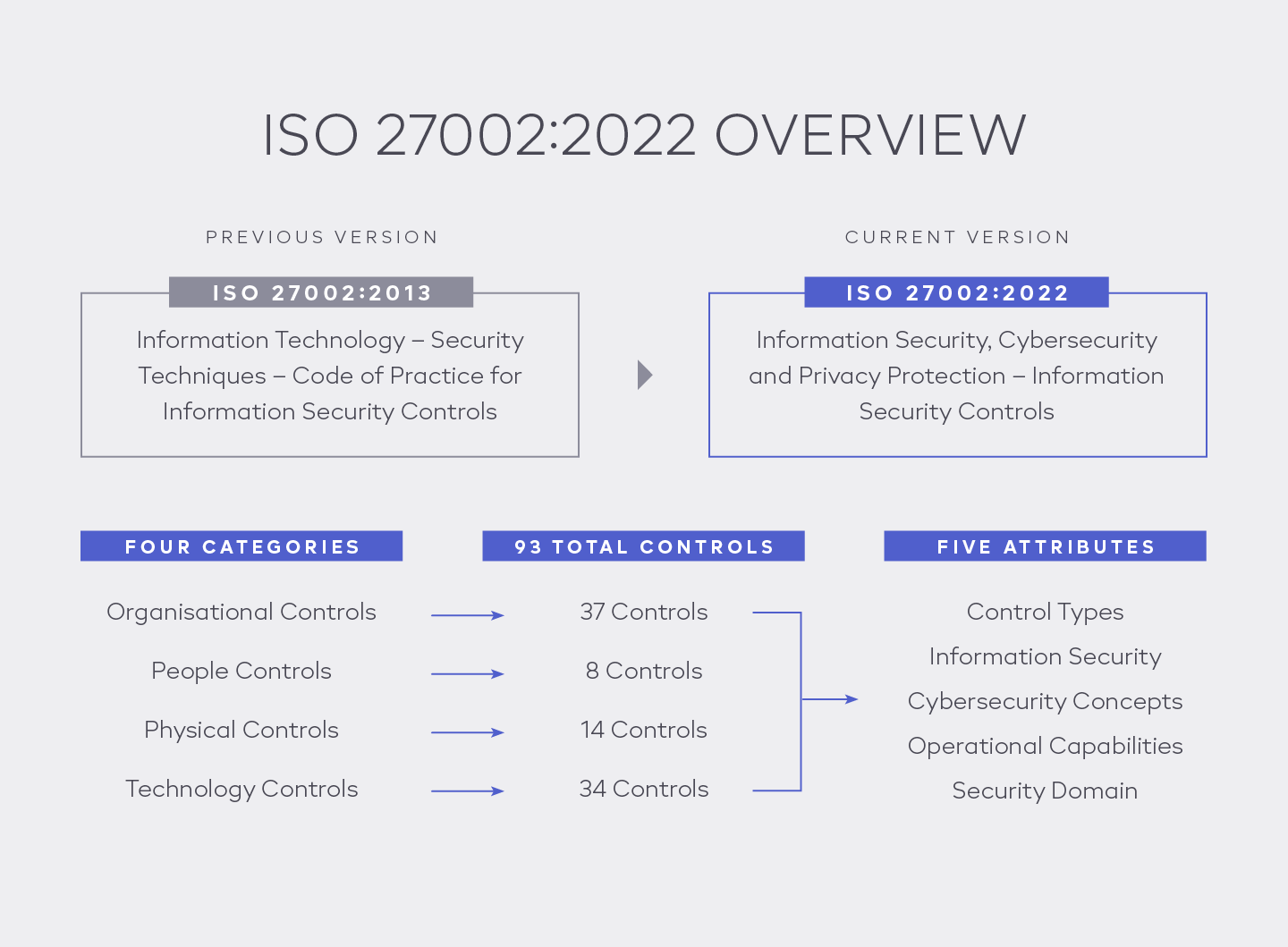
The first significant change to the standard is the move away from a “Code of Practice” and positioning it as a set of information security controls that can stand alone.
The revised standard provides a more straightforward structure that can be applied throughout an organisation. The revised version of ISO 27002 can now also be used to manage a broader risk profile. This includes information security and the more technical aspects of physical security, asset management, cyber security, and the human resource security elements that come with privacy protection.
ISO 27002:2022 Broadened Scope
The first immediate change is the name of the standard.
Previously, ISO 27002:2013 was titled “Information technology – Security techniques – Code of practice for information security controls”.
The standard is now called “Information security, Cybersecurity and privacy protection – Information security controls” in the 2022 revision.
Why has it changed?
Considering the modern compliance landscape, regulations, e.g. GDPR, POPIA and APPS and the evolving business continuity and cyber risk difficulties faced by organisations – the need for ISO 27002 to broaden the scope of its information security controls was overdue.
The objective of the latest revision (2022) was to improve the intent of the standard by providing a reference set for information security control objectives and broaden its scope for use in context-specific information security, privacy and cyber security risk management.
How ISO 27002:2022 Differs From ISO 27002:2013
Broadly speaking, the number of security controls in the new version of ISO 27002:2022 has decreased from 114 controls in 14 clauses in the 2013 edition to 93 controls in the 2022 edition. These security controls are now categorised into four control “themes.”
Controls explained
A “control” is defined as a measure that modifies or maintains risk. An information security policy, for example, can only maintain risk, whereas compliance with the information security policy can modify risk. Moreover, some controls describe the same generic measure in different risk contexts.
Get your guide to
ISO 27001 success
Everything you need to know about achieving ISO 27001 first time
Get your free guideSpecific changes in detail
The control sets are now organised into four (4) security categories or themes instead of fourteen (14) control domains. (previously A5. to A.18)
The four categories include:
- Organisational
- People
- Physical
- Technological
- 93 controls in the new version of 27002
- 11 controls are new
- A total of 24 controls were merged from two, three, or more security controls from the 2013 version; and the 58 controls from the ISO 27002:2013 have been reviewed and revised to align with the current cyber security and information security environment.
- Annex A, which includes guidance for the application of attributes.
- Annex B, which corresponds with ISO/IEC 27001 2013. It’s basically two tables table that cross-references control numbers/identifiers for ease of reference detailing what is new and what has merged.
The new controls
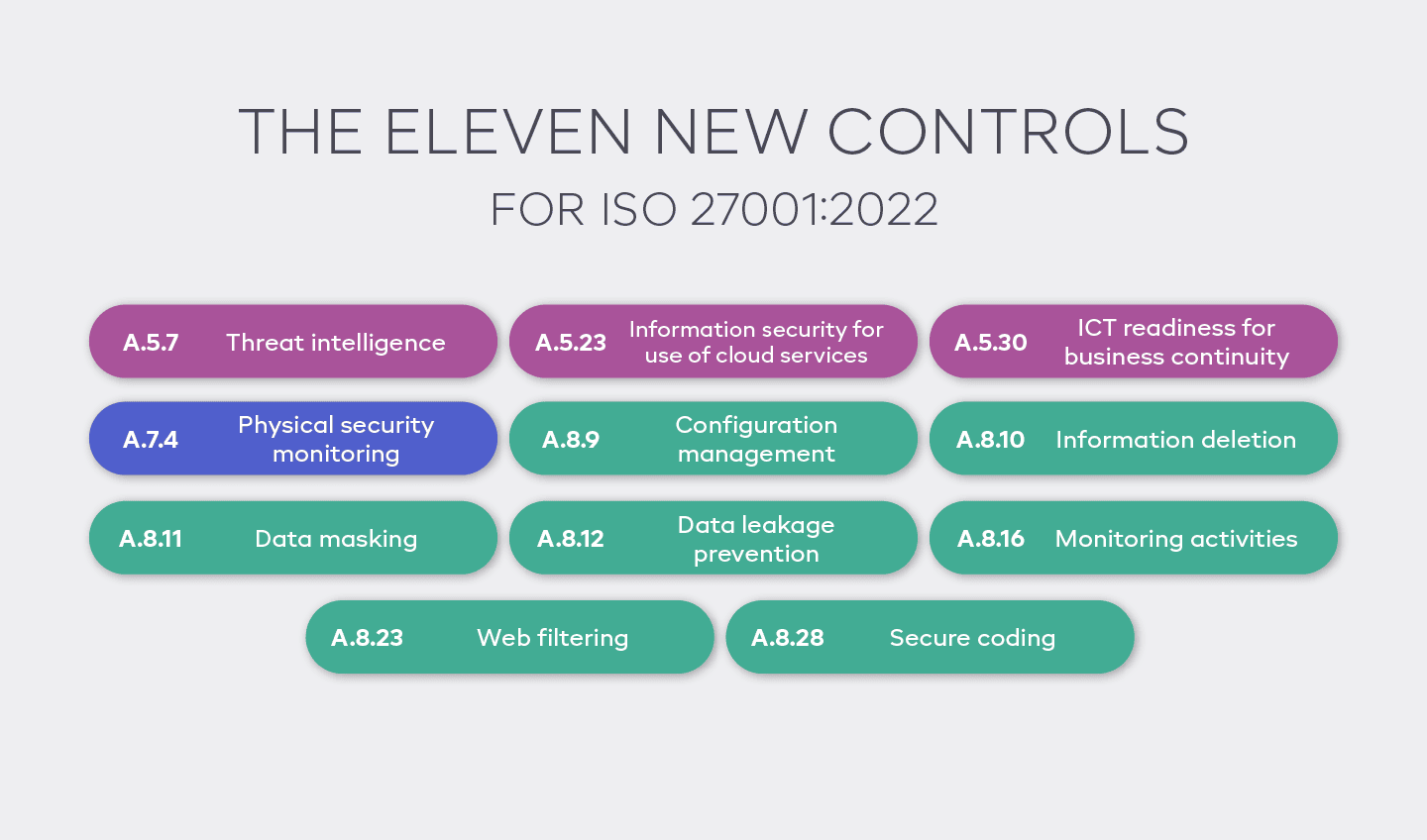
- A.5.7 Threat intelligence
- A.5.23 Information security for the use of cloud services
- A.5.30 ICT Readiness for Business Continuity
- A.7.4 Physical security monitoring
- A.8.9 Configuration management
- A.8.10 Information deletion
- A.8.11 Data masking
- A.8.12 Data leakage prevention
- A.8.16 Monitoring activities
- A.8.23 Web filtering
- A.8.28 Secure coding
Control guidance reviews & updates
The Guidance section for each control has been reviewed and updated (where needed) to reflect current developments and practices.
The language used throughout the guidance notes is more robust than the previous version; there is now a raised expectation of mandatory controls and organisations being able to evidence compliance to a greater degree. In addition, each control is now equipped with a ‘Purpose’ statement and introduces a set of “Attributes” (see 4.2) to each control.
A business implementing controls can choose which ones apply to them based on risk, as well as adding their own into an ISO 27001 compliant ISMS (context-dependent usage).
ISO 27002 themes & attributes
Attributes are a means of categorising controls. These allow you to quickly align your control selection with common industry language and standards.
These attributes identify key points:
- Control type
- InfoSec properties
- Cyber security concepts
- Operational capabilities
- Security domains
The use of attributes supports work that many companies already do within their risk assessment and statement of applicability (SOA). For example, Cybersecurity concepts similar to NIST and CIS controls can be distinguished, and the operational capabilities relating to other standards can be recognised.
Each control now has a table with a set of suggested attributes and Annex A of ISO 27002:2022 provides a set of recommended associations.
Information Security Properties
Information security involves protecting various aspects of the information, which can be represented by the CIA model. These aspects include confidentiality, integrity, and availability of the information. Understanding this enables the formulation and implementation of effective information security controls. These are now defined as attributes on a per control basis.
The CIA model explained
Confidentiality
The confidentiality of information means measures should be taken to protect it from unauthorised access. One way to achieve this is by enforcing different access levels for information based on who needs access and how sensitive the information is. Some means for managing confidentiality include file and volume encryptions, access control lists, and file permissions.
Integrity
Data integrity is an integral part of the information security triad, aimed at protecting data from any unauthorised modifications or deletions. This also involves ensuring that the unauthorised changes or deletions made to the data can be undone.
Availability
Availability aims to ensure that the data is accessible to those who need them when it is required. Some of the information security risks to availability include sabotage, hardware corruption, network failure, and power outages. These three components of information security work hand in hand, and you cannot concentrate on one of them at the expense of the others.
We'll guide you every step of the way
Our built-in tool takes you from set-up to certification with a 100% success rate.
Book a demoCybersecurity concepts
Cybersecurity concepts attributes are introduced within the 2022 revision of the standard. These attribute values consist of Identify, Protect, Detect, Respond and Recover. This aligns ISO 27002 with the ISO/IEC TS 27110, the NIST Cyber Security Framework (CSF) and other standards.
- Identify – Develop the organisation’s understanding to manage cyber security risk to systems, assets, data and capabilities.
- Protect – Develop and implement safeguards to deliver critical infrastructure services.
- Detect – Develop and implement appropriate activities to identify the occurrence of a cyber security event.
- Respond – Create and put into practice the appropriate activities to take action in response to detected cyber security events.
- Recover – Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cyber security event.
Operational capabilities
Operational capability is an attribute to view controls from the practitioner’s perspective of information security capabilities.
These include:
governance asset management, information protection, human resource security, physical security, system and network security, application security, secure configuration, identity and access management, threat and vulnerability management, continuity, supplier relationships security, legal and compliance, information security event management, and information security assurance.
Security domains
Security domains is an attribute to view controls from the perspective of four information security domains: “Governance and Ecosystem” includes “Information System Security Governance & Risk Management” and “Ecosystem cybersecurity management” (including internal and external stakeholders);
- A control may have various applications (e.g. backups help protect against malware, hacks, bugs, accidents, mechanical breakdowns, fires etc., and can include deputies and multi-skilled replacements for critical people and alternative suppliers/sources of necessary information services).
- There are typically several controls required in any given application or situation (e.g., malware can be mitigated using backups, awareness, antivirus, network access controls plus IDS/IPS and more while avoiding infection is a powerful approach if bolstered with policies and procedures).
- The controls we often use (e.g. backups) are not all-or-nothing, consisting of a number of more minor elements (e.g. backup involves strategies, policies and procedures, software, hardware testing, incident recovery, physical protection etc.).
Simplify the process with ISMS.online
Whilst many view this as the tricky part, the ISMS.online platform and support make this process intuitive. Book a platform demo to see for yourself.
Book a platform demoAnnex A explained
The Annex A table demonstrates the use of attributes, providing examples of how to assign attributes to controls, thus creating different views (per 4.2).
It is noted the filtering or sorting of the matrix can be achieved by using a tool such as a simple spreadsheet or a database, which can include more information like control text, guidance, organisation-specific implementation guidance or attributes. ISMS.online automatically facilitates these associations, making the entire process effortless.
Annex B explained
Annex B.1 and B.2 tables provide easy to navigate reference points that provide backwards compatibility with ISO/IEC 27002:2013. This makes it easy for organisations using the old management standard that need to transition to ISO 27002:2020, or for ease of reference between standards that use ISO 27002, e.g. ISO 27001, ISO 27701 similar. Again, ISMS.online automatically maps the old to new control identifiers within our platform, taking the pain out of the transition and implementation.
New Controls
| ISO/IEC 27002:2022 Control Identifier | ISO/IEC 27002:2013 Control Identifier | Control Name |
|---|---|---|
| 5.7 | New | Threat intelligence |
| 5.23 | New | Information security for use of cloud services |
| 5.30 | New | ICT readiness for business continuity |
| 7.4 | New | Physical security monitoring |
| 8.9 | New | Configuration management |
| 8.10 | New | Information deletion |
| 8.11 | New | Data masking |
| 8.12 | New | Data leakage prevention |
| 8.16 | New | Monitoring activities |
| 8.23 | New | Web filtering |
| 8.28 | New | Secure coding |
Organisational Controls
People Controls
| ISO/IEC 27002:2022 Control Identifier | ISO/IEC 27002:2013 Control Identifier | Control Name |
|---|---|---|
| 6.1 | 07.1.1 | Screening |
| 6.2 | 07.1.2 | Terms and conditions of employment |
| 6.3 | 07.2.2 | Information security awareness, education and training |
| 6.4 | 07.2.3 | Disciplinary process |
| 6.5 | 07.3.1 | Responsibilities after termination or change of employment |
| 6.6 | 13.2.4 | Confidentiality or non-disclosure agreements |
| 6.7 | 06.2.2 | Remote working |
| 6.8 | 16.1.2, 16.1.3 | Information security event reporting |
Physical Controls
| ISO/IEC 27002:2022 Control Identifier | ISO/IEC 27002:2013 Control Identifier | Control Name |
|---|---|---|
| 7.1 | 11.1.1 | Physical security perimeters |
| 7.2 | 11.1.2, 11.1.6 | Physical entry |
| 7.3 | 11.1.3 | Securing offices, rooms and facilities |
| 7.4 | New | Physical security monitoring |
| 7.5 | 11.1.4 | Protecting against physical and environmental threats |
| 7.6 | 11.1.5 | Working in secure areas |
| 7.7 | 11.2.9 | Clear desk and clear screen |
| 7.8 | 11.2.1 | Equipment siting and protection |
| 7.9 | 11.2.6 | Security of assets off-premises |
| 7.10 | 08.3.1, 08.3.2, 08.3.3, 11.2.5 | Storage media |
| 7.11 | 11.2.2 | Supporting utilities |
| 7.12 | 11.2.3 | Cabling security |
| 7.13 | 11.2.4 | Equipment maintenance |
| 7.14 | 11.2.7 | Secure disposal or re-use of equipment |
Technological Controls
ISO 27001 vs ISO 27002
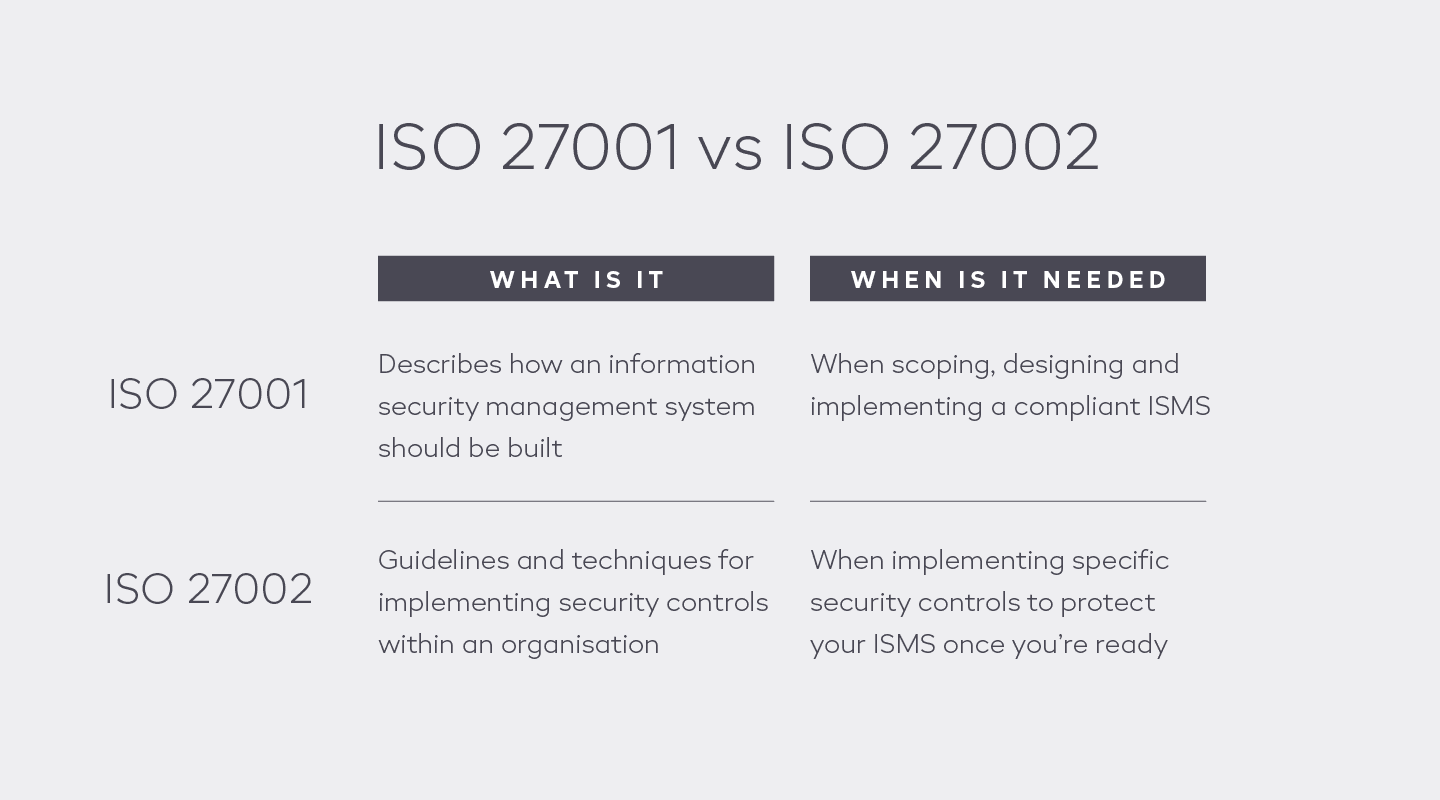
Organisations wishing to explore information security management systems may have come across both ISO 27001 and 27002 standards.
ISO 27001 is the primary standard in the 27000 family. Companies can get certified against ISO 27001 however, they cannot certify against ISO 27002:2022 since it is a supporting standard/code of practice.
ISO 27001 Annex A for example provides a list of security controls but does not tell you how to implement them, rather references ISO 27002.
ISO 27002 conversely provides guidance on implementing controls used in ISO 27001. The great thing about ISO 27002 is that the controls are not mandatory; companies can decide whether they want to use them or not, depending on if they’re applicable in the first place.
How does it affect you?
There will be a period before organisations are required to adopt the revised version of ISO 27001 for their certification audits (at least one year after publication, and typically in conjunction with their next re-certification cycle), so they have ample time to address the changes.
Ultimately, the changes should not significantly impact an organisation’s information security management system (ISMS) and ability to sustain compliance.
However, there may be an impact on the organisation’s overall control framework, specific controls, and how an organisation monitors ongoing compliance.
When converting to the new standard, organisations will need to reassess how their frameworks, controls and policies align with the new structure and updated ISO 27001/27002 controls.
The ISO 27002 2022 revision will affect an organisation as follows:
- If you are already ISO 27001 2013 certified
- Are you are mid certification
- If you are about to re-certify
- If you are already ISO 27001:2013 certified
If your organisation is already certified, you do not need to do anything now; the revised ISO 27002 2022 standard will be applicable upon renewal/re-certification. It, therefore, stands to reason that all certified organisations will have to prepare for the revised standard at upon recertification or if adopting new sets of controls or standards e.g. ISO 27701 or similar.
Get an 81% headstart
We've done the hard work for you, giving you an 81% Headstart from the moment you log on.
All you have to do is fill in the blanks.
How does it affect your (re)certification?
Suppose an organisation is currently in the ISO 27001 2013 certification or re-certification process. In that case, they will be expected to revisit their Risk Assessment and identify the new controls as applicable and revise their’ Statement of Applicability’ by comparing the revised Annex A controls.
Since there are new controls, merged controls and modified or additional guidance to other controls, organisations need to review the revised ISO 27002:2022 standard for any implementation changes.
Even though ISO 27001 revision 2022 is yet to be published, Annex B of ISO 27002 maps controls the standard’s 2013 and 2022 versions.
Your statement of applicability (SOA) should still refer to Annex A of ISO 27001, while the controls must reference the ISO 27002:2022 revised standard, which will be an alternative control set.
Do you need to amend your documentation?
Complying with these changes should include:
- An update to your risk treatment process with updated controls
- An update to your Statement of Applicability
- Update your current policies and procedures with guidance against each control where necessary
How does it affect your ISO 27001:2013
Until a new ISO 27001 2022 standard is published, the current ISO certification schemes will continue, though mapping to the new ISO 27002 2022 controls will be required via Annex B1.1 & B1.2 however ISO experienced auditors will recognise the structure of the controls, therefore will have more to work with. Adoption of ISO 27002:2022 could make for a smoother audit.
Upcoming changes to ISO 27001
Most information security experts expect that the ISO 27001 changes will be minor textual changes with a minor update of Annex A to align with the ISO 27002 2022 revision.
The main part of the ISO 27001, which includes clauses 4-10, will not change. These clauses include scope and context, information security policy, risk management for resources such as training & awareness about communication and document control to monitoring and measurement of operational activities by an internal audit department to corrective actions.
Only the controls listed in ISO 27001 Annex A and ISO 27002 will be updated.
Changes in ISO 27001:2022 Annex A will be fully aligned with changes in ISO 27002:2022
Are any other 27000 standards affected?
Management system standards and frameworks related to and based on the ISO/IEC 27002:2013 version will feel the change.
The changes will have an additional impact when they cascade to related standards such as ISO 27017 cloud security, ISO 27701 privacy, and various national standards that have adopted or incorporated the current requirements and guidance.
That should occur as the review and update cycles for those standards occur over the next few years, and further impact may be expected for local standards and frameworks.
Demonstrating good practice for ISO 27002
Physical and Environmental
The physical and environmental aspects of an organisation are critical in determining its information security. The proper controls and procedures will ensure the physical safety of an organisation’s information by restricting access to unauthorized parties and protecting them against damages such as fires and other disasters.
Some of the information security techniques include:
- Measures must be taken to monitor and restrict the physical access to the organisation’s premises and support infrastructures, such as air conditioning and power. This will prevent and ensure the detection and correction of unauthorised access, vandalism, criminal damage, and other tampering that could occur.
- Sensitive areas must be given partial access and the list of authorised individuals periodically reviewed and approved (at least once a year) by the Physical Security Department or the Administration.
- Video recording, photography, or any other form of digital recording should be prohibited in restricted areas except with the permission of the relevant authority.
- Surveillance should be set around the premises at places such as entrances, exits and restricted areas. These recordings should be monitored round the clock by trained personnel and stored for at least a month in case a review is needed.
- Restricted access in form of access cards should be provided to allow time-limited access to vendors, trainees, third parties, consultants and other personnel authenticated to access the areas.
- Visitors to the organisations should be accompanied at all times by an employee except when using open areas such as the reception foyer and restrooms.
Human Resources
These measures aim at ensuring the organisation’s information is safe as far as the employees of the organisation are concerned.
Some human resource information security standards include:
- Each employee should be vetted before employment to verify their identity, their professional references, and their overall conduct. These should especially be rigorous if they are to take up trusted information security positions in the organisation.
- The employees should all agree to a binding non-disclosure or confidentiality agreement. This will dictate the level of discretion they handle the personal and proprietary information they come in contact with in the course of their employment.
- The Human Resource department must inform the Finance, Administration and other relevant departments when an employee is hired, suspended, fired, transferred, on long-term leave and any other circumstances that could require the changing of their permissions.
- Once the HR department informs the other departments of the change of an employee’s status, this should be followed by the adjustment of the relevant physical and logical access rights.
- Employees’ managers should follow-up to ensure all the keys, access cards, IT equipment, storage devices and all other company assets are returned before the termination of their employment.
Access Control
Access control involves the passwords, key cards, or other security restrictions designed to limit the accessibility of the company’s information and systems.
Some of them include:
- The access to corporate networks, IT systems, information, and application should be controlled based on the role of the users or as specified by the relevant information asset owners or organisational procedures.
- Restrictions must be set to alert the system and/or lock out user accounts after a predefined number of failed login attempts. These should be followed up on to eliminate the risk of an attempted breach.
- All corporate workstations/ PCs should have password-protected screensavers with timeouts of less than 10 minutes of inactivity.
- The privileged access rights such as for those required tasked with the administration, configuration, management, security, and monitoring of the IT systems should also be reviewed periodically by the relevant Information Security body.
- The passphrases and passwords must be complex and lengthy with a combination of numerals, letters and special characters to make them impossible to guess. These should not be stored in any written or readable format.
- The organisation should disable all write access to removable media such as CD/DVD writers on all the company computers unless authorised for specific business reasons.
Next Steps
In terms of the next steps, the main activities to perform include the following:
- Purchasing the updated standard.
- Review the new ISO 27002 standard and its control changes.
- Conduct a risk assessment/analysis.
- To mitigate any identified risks, select the most appropriate controls and update your ISMS policies, standards etc., accordingly.
- Update your Statement of Applicability (SoA).
This will help you get ahead of the game for re-certification or adoption of additional ISO 27000 family standards/frameworks, e.g. ISO 27018, 27017, 27032, which are widely expected to be updated shortly after the ISO 27001:2022 revision.
Get an 81% headstart
We've done the hard work for you, giving you an 81% Headstart from the moment you log on.
All you have to do is fill in the blanks.
FAQs
Who can implement ISO 27002
ISO/IEC 27002:2022 is designed for anyone who initiates, implements, or maintains an ISMS system. By adopting this updated version, you can establish security controls that are robust, relevant, and suitable for your organisation’s environment.
Organisations of all sizes and security maturity levels can benefit from adhering to the ISO 27002 code of practice. At ISMS.online, we’re here to help you successfully implement ISO 27002:2022.
How to Get Started With ISO 27002
Embarking on the ISO 27002 journey is straightforward. At ISMS.online, we recommend these eight steps for a smooth implementation:
- Understand the ISO 27002 standard: ISO 27002 is an international standard offering guidelines for selecting and implementing information security controls and practices. Applicable to organisations of all industries and sizes, it helps develop information security management guidelines tailored to your specific context.
- Study the control categories: ISO 27002:2022 presents four categories of information security controls: organisational, people, physical, and technological.
- Obtain the ISO 27002:2022 standard: Purchase the complete ISO 27002:2022 standard from the ISO’s website.
- Understand the relationship between ISO 27001 and ISO 27002: ISO 27001 outlines objectives or goals for information security management, while ISO 27002 provides detailed guidance on implementing the controls required to meet those objectives.
- Get trained and certified: Enrol in ISO/IEC 27002 training courses to gain the necessary knowledge for selecting, implementing, and managing the controls specified in the standard.
- Implement the controls: Utilise the guidelines provided in ISO 27002:2022 to select and implement the appropriate controls for your organisation’s specific context.
- Stay updated on revisions and updates: ISO 27002 undergoes revisions to account for changes in technology, legal requirements, and best practices. Ensure you stay updated on new versions and incorporate any relevant changes into your organisation’s information security management system.
- Monitor and improve: Continually monitor the effectiveness of your information security management system and make improvements as needed.
Discover how ISMS.online can assist you in getting started with ISO 27002:2022 implementation.
Is Certification ISO 27002 Possible
Certification for ISO 27002 is not possible, as it is not a management standard and does not define how to run a system.
However, ISO 27002:2022 plays a crucial role in helping organisations like yours meet ISO 27001:2022 certification requirements.
At ISMS.online, we provide guidelines for implementing, managing, and continually improving your information security management system.
Are there any ISO 27002 Requirements
The ISO 27002:2022 standard does not have any explicit requirements for organisations.
It only offers suggestions that organisations should implement as per the nature of their specific information security risks.
With ISMS.online you can find out what security risks your organisation should be aware of.
What are the national equivalents of ISO 27002
There are various standards in various countries that are equivalent to ISO 27002. Despite local publication and translation delays which lead to these equivalents coming months after the revision and release of the main ISO/IEC standard, national bodies ensure that the content is translated accurately to reflect ISO 27002 in its entirety.
Below are some of the national equivalent standards for ISO 27002 in various countries:
- Argentina – IRAM-ISO-IEC 27002:2008
- Australia and New Zealand – AS/NZS ISO/IEC 27002:2006
- Brazil – ISO/IEC NBR 17799/2007 – 27002
- Indonesia – SNI ISO/IEC 27002:2014
- Chile – NCH2777 ISO/IEC 17799/2000
- China – GB/T 22081-2008
- Czech Republic – ČSN ISO/IEC 27002:2006
- Croatia – HRN ISO/IEC 27002:2013
- Denmark – DS/ISO27002:2014 (DK)
- Estonia – EVS-ISO/IEC 17799:2003, 2005 version in translation
- Germany – DIN ISO/IEC 27002:2008
- Japan – JIS Q 27002
- Lithuania – LST ISO/IEC 27002:2009 (adopted ISO/IEC 27002:2005, ISO/IEC 17799:2005)
- Mexico – NMX-I-27002-NYCE-2015
- Netherlands – NEN-ISO/IEC 27002:2013
- Peru – NTP-ISO/IEC 17799:2007
- Poland – PN-ISO/IEC 17799:2007, based on ISO/IEC 17799:2005
- Russia – ГОСТ Р ИСО/МЭК 27002-2012, based on ISO/IEC 27002:2005
- Slovakia – STN ISO/IEC 27002:2006
- South Africa – SANS 27002:2014/ISO/IEC 27002:2013[3]
- Spain – UNE 71501
- Sweden – SS-ISO/IEC 27002:2014
- Turkey – TS ISO/IEC 27002
- Thailand – UNIT/ISO
- Ukraine – СОУ Н НБУ 65.1 СУІБ 2.0:2010
- United Kingdom – BS ISO/IEC 27002:2005
- Uruguay – UNIT/ISO 17799:2005















