What is a Statement of Applicability?
Put simply, in its quest to protect valuable information assets and manage the information processing facilities, the SoA states what ISO 27001 controls and policies are being applied by the organisation. It benchmarks against the Annex A control set in the ISO 27001 standard (described at the back of that ISO standards document as reference control objectives and controls).
The statement of applicability is found in 6.1.3 of the main requirements for ISO 27001, which is part of the broader 6.1, focused on actions to address risks and opportunities.
The SoA is therefore an integral part of the mandatory ISO 27001 documentation that needs to be presented to an external auditor when the ISMS is undergoing an independent audit e.g. by a UKAS audit certification body.
Who does ISO 27001 apply to?
ISO 27001 is applicable to all types and sizes of organisations, including public and private companies, government entities and not-for-profit organisations. The common thread regardless of organisation size, type, geography or sector is that the organisation is aiming to demonstrate best practice in its approach to information security management. Best practice can be interpreted differently of course.
The ISO standard is all about developing a system for the management of information security risk. So depending on the organisation leadership appetite for information risk and the scope of assets to address risks around, the controls and policies applied may vary considerably from one organisation to another, yet still meet the ISO 27001 control objectives.
What is clear though is that the achievement of ISO 27001 certification through an independent audit from an approved ISO certification body, will mean the organisation has reached a recognised level of control (best practice as a standard) for the information assets and processing facilities.
ISO 27001 certification gives interested parties such as powerful customers and prospects a higher level of confidence than self developed methods or alternative standards that do not carry the same independent audit or international recognition.
Get your guide to
ISO 27001 success
Everything you need to know about achieving ISO 27001 first time
Get your free guideWhy is the SoA important?
Together with the Scope of the information security management system, (4.3 of ISO 27001), the SoA provides a summary window of the controls used by the organisation. The SoA is a core requirement to achieve ISO certification of the ISMS and along with the scope will be one of the first things that an auditor will look for in their audit work.
This documentation will need to be available for review during the Stage 1 certification audit, although will only be drilled into during the Stage 2 audit, when the auditor will be testing some of the ISO 27001 controls and ensuring they not only describe, but adequately demonstrate the control objectives are being achieved.
The auditor will review the information asset inventory, consider the risks, their evaluation & treatments, and look for physical evidence that the organisation has satisfactorily implemented the controls it has claimed to address the risk.
The SoA and Scope will cover the organisation’s products & services, its information assets, processing facilities, systems in use, people involved and the business processes, whether that is a virtual one person business or a multi-site international operation with thousands of staff.
Powerful educated customers with significant information risk (e.g. because of GDPR or other commercial information assets) may want to see the Scope and SoA before buying from a supplier, to ensure that the ISO certification does in fact address the areas of the business involved with their assets.
It’s no good having an ISO certification with a Scope and SoA for a UK head office when the actual information processing risk is taking place in an offshore building with resources out of scope! That is actually one of the reasons why the certification bodies are now encouraging ‘whole organisation’ Scopes, which of course may mean a much broader and deeper statement of applicability is required.
In summary, a well presented and easy to understand SoA shows the relationship between the applicable and implemented Annex A controls given the risks and information assets in scope. It will give huge confidence to an auditor or other interested party that the organisation is taking information security management seriously, especially if that is all joined up into a holistic information security management system.
What is Annex A ISO 27001?
Annex A of ISO 27001 is a catalogue of the information security control objectives and controls that need to be considered during the ISO 27001 implementation. The technical term used for ISO is about ‘justification’ of the control, The SoA will show whether the Annex A control is:
- Applicable and implemented as a control now
- Applicable but not implemented as a control (e.g. it might be part of an improvement for the future and captured in 10.2 as part of an Improvement, or the leadership are prepared to tolerate the risk given their other implemented control priorities)
- Not applicable (note that if something is considered as not applicable, the auditor will look to understand why that is so a documented record should be kept about that too in the SoA).
The controls need to be reviewed and regularly updated over the course of the 3 year ISO certification lifecycle. This is part of the ongoing information security management improvement philosophy embedded into the standard. Given the increasing pace of growth in cyber crime, cyber security also moves quickly too so anything less than an annual review of controls would potentially increase the organisation’s threat exposure.
How many controls are there in ISO:27001?
There are 114 Annex A controls divided into 14 different categories. The ISO 27001 Annex A Controls are listed below.
- A.5 Information security policies
- A.6 Organisation of information security
- A.7 Human resource security
- A.8 Asset management
- A.9 Access control
- A.10 Cryptography
- A.11 Physical and environmental security
- A.12 Operations security
- A.13 Communications security
- A.14 System acquisition, development, and maintenance
- A.15 Supplier relationships
- A.16 Information security incident management
- A.17 Information security aspects of business continuity management
- A.18 Compliance
Which controls should I include?
The Statement of Applicability is the main link between your information security risk assessment and treatment work, and shows ‘where’ you have chosen to implement information security controls from the 114 control objectives. (A good SoA will also be able to drill in to show ‘how’ they have been implemented as well.)
Whilst the Annex A controls provide a useful checklist for consideration, just implementing all 114 controls from the ‘bottom up’ may be expensive and miss the fundamental aims of the standard. Sadly some information security consultants and providers peddling ‘complete ISO 27001 documentation toolkits’ will advocate this approach but it’s the wrong way to do information security management.
There is a reason why the core requirements in ISO 27001 from 4.1-10.2 are there. They help take the organisation on the business and strategy led approach where you look from the top down. Having considered the issues, the interested parties, the scope and the information assets, the organisation can identify the risks, then evaluate them and consider treatments for those risks.
The risks around the valuable information and the processing facilities, devices, people involved etc should be evaluated with the Confidentiality, Integrity, and Availability (CIA) of information in mind.
This breakdown of the CIA is also an important aspect for the auditor to understand and demonstrates the organisation has more holistically considered the risk. Crucially it also means the SoA has been developed with that more comprehensive approach, rather than just one part e.g. only considered the risk to loss of information from a breach.
Whilst the organisation will consider the risks from its operations as drawn out from above it is worth mentioning that one of the control areas in Annex A that will always be applicable is the “Identification of applicable legislation and contractual requirements” in A.18.1.1. This will mean you also consider the requirements of relevant laws, regulations and contractual requirements. That is gaining much more prominence because of EU GDPR for those processing EU Citizen information and increasingly all over the world too with other privacy standards such as POPI in South Africa, LGPD in Brazil, and the CCPA in California.
In understanding the expectations of the privacy regulations, it also effectively dictates that many of the ISO 27001 controls are required, whether you think they are or not. So a smart auditor will expect an understanding of the Applicable Legislation affecting your organisation and how that is also informing your choice of applicable controls in the SoA justification.
Some information security risks could of course be terminated entirely, transferred to another party, treated or tolerated. All those Annex A controls then help you consider and where appropriate, implement the transfer, treat or tolerate philosophy around the risks. The SoA then shows which security measures from the Annex A controls you are using and how you have implemented them i.e. your policies and procedures.
The Annex A control objectives and controls as listed in the ISO 27001 standard are not prescriptive but do need to be considered and that justification for applicability is essential for an independent certification from an ISO certification body.
Get an 81% headstart
We've done the hard work for you, giving you an 81% Headstart from the moment you log on.
All you have to do is fill in the blanks.
ISO 27002 and the Statement of Applicability
Whether independent certification is a goal or perhaps simply compliance when coupled with the complementary ISO 27002 guidance the Annex A controls are a positive foundation to build on for any organisation that wants to improve its information security posture and do business more securely.
ISO 27002, is the supplementary standard to ISO 27001, provides a code of practice and useful outline for information security controls and thus provides a very good catalogue of control objectives and controls for the treatment of risks as well as guidance on how to implement them.
What security measures (Annex A controls) you deploy to manage those risks will actually depend on your organisation, its risk appetite and the scope as well as the Applicable Legislation. But whatever it is, it needs to be presented in the Statement of Applicability if you want to achieve an ISO 27001 certification!
What information needs to be included in the SoA?
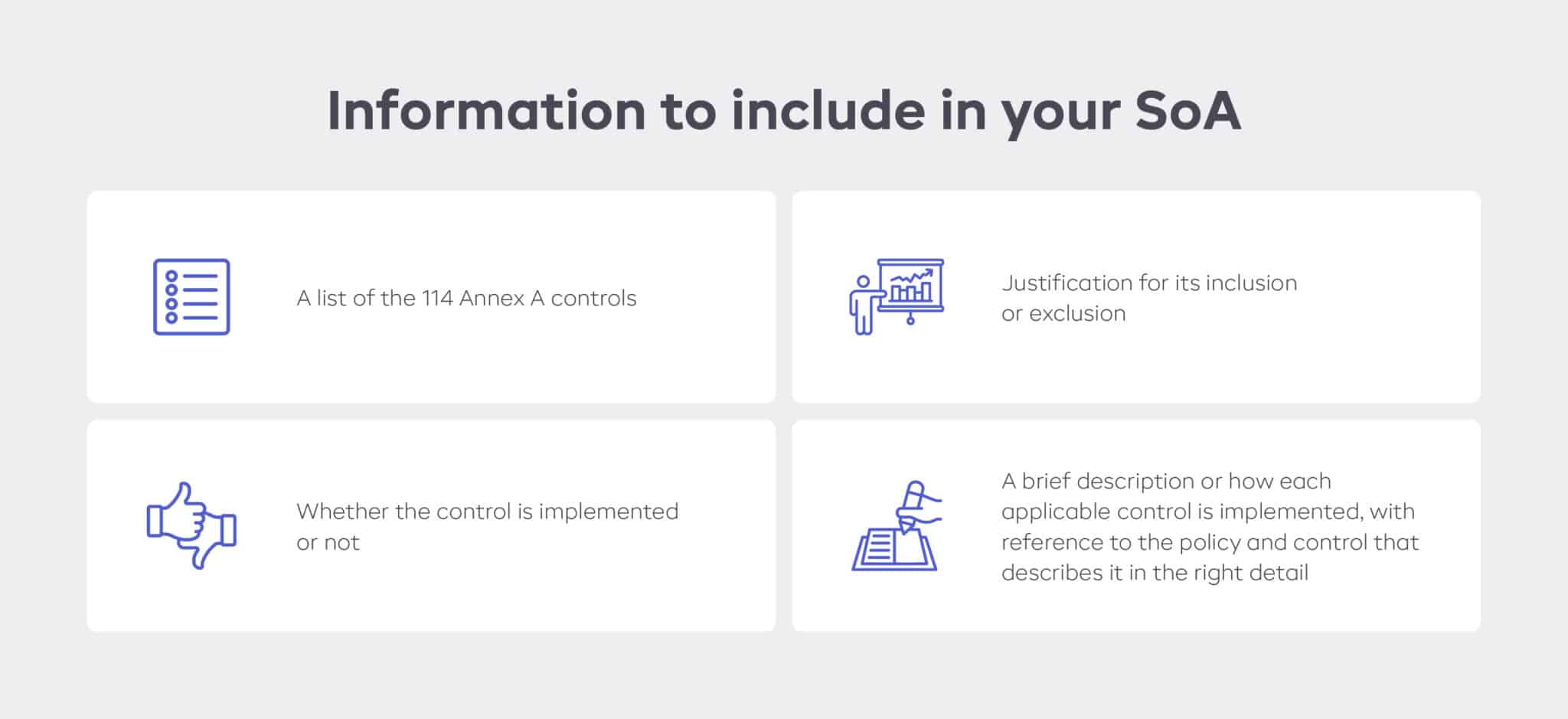
So let’s summarise what information needs to be included as a minimum for the SoA.
- A list of the 114 Annex A controls
- Whether the control is implemented or not
- Justification for its inclusion or exclusion
- A brief description or how each applicable control is implemented, with reference to the policy and control that describes it in the right detail
As mentioned above the SoA is a window into the organisation’s ISMS. If you are unable to show how that window opens into the depth and connected nature of the information security management system that can create problems. Imagine the situation when the auditor turns up and the spreadsheet showing the 114 controls is well out of date with the actual management controls in place.
One of the most common reasons for failing an ISO 27001 audit is because the auditor is unable to draw confidence in the administration of the ISMS and documentation is poorly managed or missing. Having a standalone SoA ‘document’ rather than integrated and automated documentation of an SoA increases that risk.
How do you create the Statement of Applicability?
As long as the SoA has the right information, is accurate and is up to date, you can create the SoA from paper, spreadsheets, documents, or professional systems that automate it as part of their broader GRC (Governance, Regulation & Compliance) capability.
In an ideal world your SoA will hardly change (not least because certification bodies may charge for version changes of the SoA). However, what sits underneath the SoA i.e. the beating heart of the ISMS itself should be dynamic as a living breathing representation of your evolving information security landscape.
The SoA needs to be reviewed when your policies and controls are reviewed (at least annually) so it would still benefit from being an efficient process given the 114 controls for consideration.
Knocking up a spreadsheet with the controls as a checklist is a piece of cake and pretty quick to do. However doing that with confidence that all the earlier information security planning and implementation work around the assets, risks and controls has been done in the right order and expressed as the summary SoA is not quite so straightforward. An auditor will want to see what sits beneath the simple topline of 114 rows in a spreadsheet.
In the old days presenting the SoA as a 200 page verbose document really did mean a lot of work especially to keep it updated as the policies and controls evolved. There are now much better and easier ways to automate the SoA and take advantage of the hard work already done in other parts of the ISMS.
How to save time when writing your Statement of Applicability
The SoA typically takes a long time for an organisation to put together because of what informs it. If we think about the steps involved in its creation, and the work needed for that, it’s little wonder:
- Consider the issues, interested parties and scope of the ISMS
- Identify the information assets and processing facilities & devices at risk
- Evaluate and assess the risks associated with the security of the information using the Confidentiality, Integrity and Availability
- Assess those risks and then decide on which of the 114 Annex A controls are needed
- Understand and evaluate applicable legislation (and any key contract obligations from powerful customers) to highlight other control areas
- Decide on how to implement the control in terms of policy, procedure, people, technology etc
- Then create the SoA document itself with those justifications about applicability being clear
- Ideally linking to the control detail, the risks and the assets to show the ISMS working
- And manage it on an ongoing basis.The SoA is one small but very important part of a very comprehensive ISMS. Done well it will set the organisation up for audit success and confidence building for smart customers and other stakeholders. Done badly it will almost certainly disrupt and delay time to certification and may mean loss of business or future opportunity from failure to achieve or maintain certification.

Speed up the SoA process with ISMS.online
ISMS.online is a comprehensive information security management system that amongst many other things eases the administration and management of your information assets, risks, policies and controls, all in one place.
It also means the creation of the SoA can be automated and presented simply and efficiently. Therefore in addition to other benefits like costing less time to achieve ISO 27001 success, it speeds up the ISO Certification journey too.
Focus your energy on running your business the way you want to, and spend time on what you need to achieve for success, worrying less about how to do it. ISMS.online makes it all so easy to get your work done, including the SoA at a fraction of the cost and time of alternatives.
Book a platform demo








