
ISO 27001 Simplified: Assured Results Method (ARM) Guide
Table Of Contents:
- 1) Implementing ISO 27001 and unsure where to start?
- 2) So what are the possible paths for implementing your ISO 27001 ISMS?
- 3) Aim for pragmatism not perfection with your first ISMS
- 4) How to follow ARM for fast and effective ISO 27001 success
- 5) What happens after the ISO 27001 Stage 2 Audit?
- 6) « The ISO 27001 Document Toolkit
- 7) Satisfy The Data Security and Protection Toolkit 2018 »
Implementing ISO 27001 and unsure where to start?

So what are the possible paths for implementing your ISO 27001 ISMS?
A popular route is the ‘information security management gap analysis’, where you’ll put a lot of time and money into finding the gaps. But you still only get a gap analysis (probably with results in a hard to navigate, and manage spreadsheet) not any movement forward, to establishing your ISMS. There is a better way.
Another common path is, by avoiding the gap analysis, and just going into delivery. Some organisations start by creating all the 114 Annex A controls, putting in place policies, processes, and procedures first. However, this is also sub-optimal and can be time-consuming, especially if the business has no risks where those controls would be applicable. This is a ‘bottom-up’ approach, and we’d always suggest that it follows the ‘top-down’ core requirements.
The ISO standard starts to lead you through the top-down process well if you do start at the beginning with the ISO 27001 core requirements. However, the core requirements (management clauses) cover operation beyond implementation, so will divert attention to considering post-certification activities (such as monitoring, internal audit, review and improvement) before you even start to operate your ISMS. This is better, but not the best way when you are in a hurry or want to follow the most expedient path. There is a better way to assure results, that takes the best from all the common practices, and avoids the waste from a gap analysis. We call it the Assured Results Method – ARM.
Aim for pragmatism not perfection with your first ISMS
Often, but not always, there is an outside driver for achievement of ISO 27001, such as a tender requirement or customer pressures given a change in risk appetite with the supply chain (e.g. because of cybercrime or regulation such as GDPR). Those outside drivers usually mean tight timescales, so perfection is often the enemy of the good when it comes to achieving ISO 27001 certification success to a compressed deadline, especially if after an independent certification.
ISO 27001, like the other ISO management standards, is all about continuous improvement and is fundamentally a risk management based standard. So being pragmatic about the business risk (assuming that is also acceptable to customers), and showing improvement as part of the management system, is well received by auditors. It also shows an organisation is in control and aware of its risks. As such, the ARM emphasises the pragmatic over the perfect and allows you to easily build on what you have today. Then you plan for improvements over time, prioritised from a risk perspective.
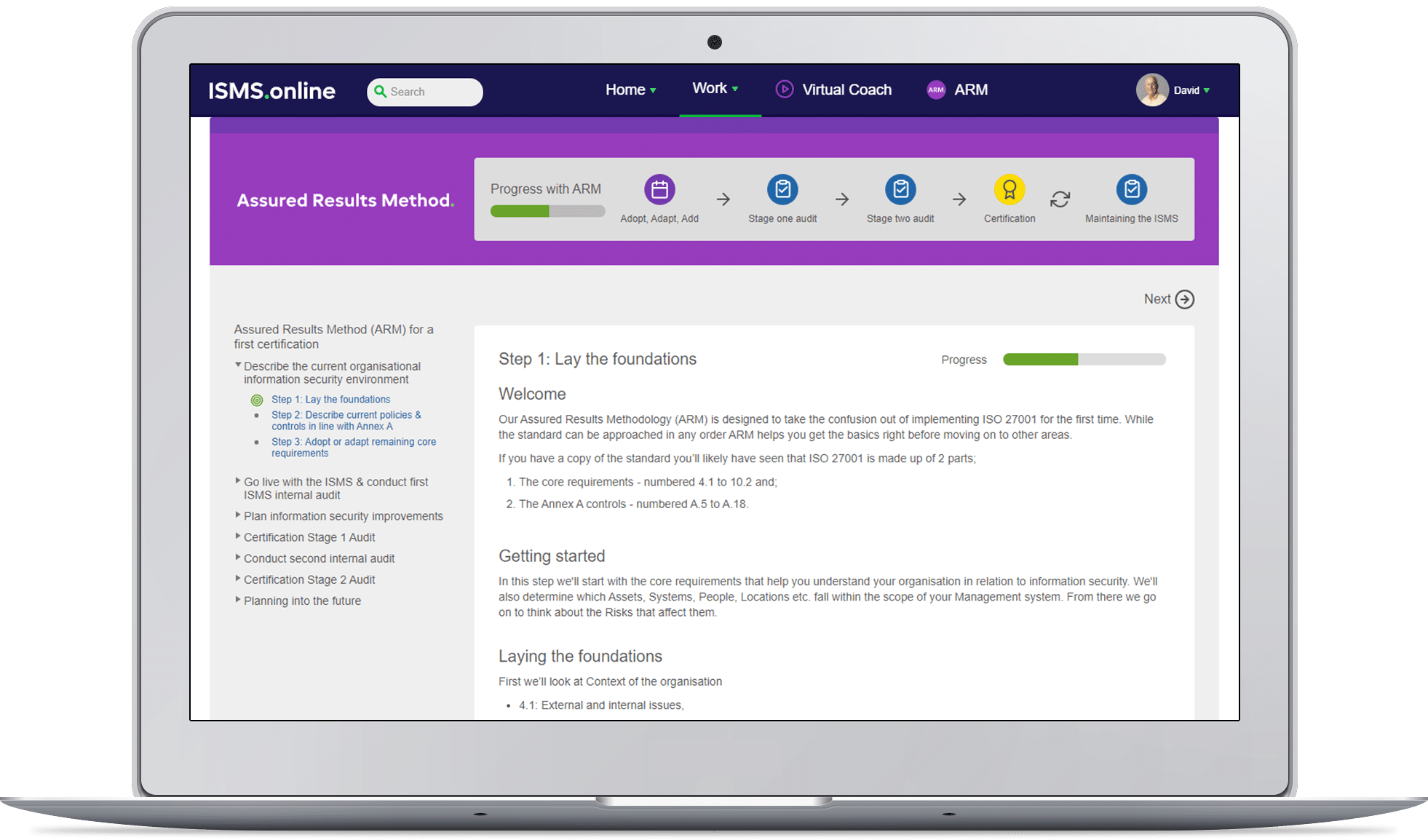
If you don’t already do enough today then the pre-configured ISMS.online platform, the included actionable documentation and the optional Virtual Coach services will help you get results much quicker and at lower total cost than any other alternatives. The Virtual Coach also includes the ARM steps to success as well, which are summarised below.
How to follow ARM for fast and effective ISO 27001 success
Step 1: Describe the current organisational information security environment
A: Lay the foundations for information security management success
This means you understand your organisation and the relevance of information security to it. It includes considerations for parties that will be interested in your information security management, the information assets that you need to protect, the risks you face and your top-level Information Security Policy.
Practically this includes addressing Clause 4, Clause 5, and Clause 6 of the ISO 27001 standard along with Annex A 8, which focuses on the information classification and information asset inventory. If you can’t already do this, the ISMS.online platform contains a lot of content and tools that will help you rapidly describe these areas. It also offers up a bank of the most common information security risks, links to the relevant Annex A controls, and crucially ensures you take an approach to your implementation that is right for your business culture, risk appetite and desired ways of working.
B: Describe current information security policies and controls
You will already have some policies and controls in place, even if they are implicit rather than well documented. These are most likely based on consideration for risks or perceived “best practice” and the knowledge of professional employees, or just simply common sense approaches around protecting your valuable information from malicious parties. It may not have been done through a formal risk assessment or documented approach. So, for this step, you simply need to describe what you do today, in the context of the standard’s policies and controls in Annex A, and then link it back to the information assets and headline risk work you’ll do in laying the foundations.
If you can’t easily describe how you work today in the relevant information security areas based on your risk analysis, you’ll also be unable to demonstrate it in the Stage 2 audit so an external auditor will have no choice but to issue non-conformities and potential failure notices. It is one of the common problems facing organisations that just purchase information security policy document toolkits, then dump them in a shared drive and think that is good enough for success; it is not. The actionable documentation, content and prebuilt tools within the ISMS.online platform for the Annex A controls will help guide your thinking. They also give you the chance to adopt, adapt or add to it, saving huge amounts of time and crucially making sure it is right for your business to be able to demonstrate in practice too.
C: Adopt or adapt the remaining core requirements of ISO 27001
Now you can go back and describe how you will approach the remaining core requirements of the standard, which are focused more on the operational administration and ongoing improvement of the information security management system. It includes how you’ll address some administratively painful but important aspects of the ISMS as well as clarifying the leadership and roles supporting the information security management system. The potentially painful administration includes documenting the Statement of Applicability for ISO 27001 clause 6.1.3 as well as the processes for meeting information security objectives in clause 6 of the core requirements. This part also addresses how the operation is managed, internal audits, management reviews, corrective actions, nonconformities and improvements are undertaken.
Like the other parts of ISO 27001, ISMS.online has already addressed much of the requirements here, meaning a relatively pain-free approach, with automated reporting, and practical pre-configured workspaces to demonstrate that effective operation easily. It goes a long way to helping you achieve this final set of requirements in as short a timeframe as possible.
Step 2: Go live with the ISMS
The sooner you can move your information security management system into operational mode, the quicker it can become ‘business as usual’ and show you are taking information security seriously. It is likely that your ISMS will begin operation organically with processes, controls and policies being introduced throughout the implementation period, however, it is beneficial to state a date when the ISMS is considered “Live & Operational”.
The benefits are:
- A clearly defined “start” point before which the auditors should not consider within the scope of the ISMS audit and should not document findings of non-compliance prior to this date
- It focuses on responsible parties within the organisation from when they are expected to start providing evidence for controls within their area of responsibility
- Anything prior to this date can be referenced during an audit by you as “early adoption”
You do not have to be “perfect” at the “go-live” date, but it worth selecting a date when a majority of processes, policies and controls are ready for operation. Clearly, improvements can still be made between this date and the Stage 1 or Stage 2 audit.
Ideally, the date should be at least 1 month prior to the Stage 1 audit (which is usually 1 month prior to the Stage 2 audit). This is to ensure that by the time of the Stage 2 audit, at least 2 months’ worth of evidence has been accumulated.
Agree and document the formal “launch” date of the ISMS. If you are using ISMS.online we suggest you capture and record that in your ISMS Board area and also announce it to your staff in scope e.g. via your ISMS.online Group communications and reference it for the auditor to see if requested.
Step 3: Plan information security improvements
During the work to describe your current information security implementation, it is very likely that you will have identified improvements that you need or wish to make. These might be to further reduce your risks to an acceptable level, to improve operational efficiency or even take advantage of new opportunities. Rather than slow down to improve at the time, you’d have made notes about these areas for improvement and it’s now time to plan those information security improvements. This will show you are in control of the ISMS and demonstrate to your senior management as well as an external auditor you are continuously improving.
In ISMS.online it encourages these improvements to be recorded in the “Corrective Actions & Improvements Track” (or if very simple then added them as tasks within the relevant risk treatment plan.) To demonstrate that effective control and planning you should now review all the items and assign owners, prioritise them for action, setting target dates for completion.
During the prioritisation exercise, the following should be considered:
- How easy the improvement implementation will be
- How much risk-reduction or other benefits will be achieved
- If the improvement implementation can be completed after certification (where the risk owner is happy to accept the above-target risk level until implementation is complete)
- If the implementation needs to be completed before the ISO 27001 Stage 1 Audit (improvements to the description of controls)
- If the implementation needs to be completed before the ISO 27001 Stage 2 Audit (improvements to the implementation & operation of controls)
Where identified improvements are necessary prior to the Stage 1 or Stage 2 Audit, you should be comfortable that this can be achieved before booking the relevant Audit. (Stage 1 and Stage 2 Audits are normally about 1 month apart).
Having completed Step 3 you’ll be in a really good place for succeeding in the Stage 1 audit.
Step 4: ISO 27001 Stage 1 and Stage 2 Audits
What is the Stage 1 Audit for ISO 27001?
Having completed Steps 1-3, you’ll be in a great place for the Stage 1 Audit. The certification body auditor will want to see the Information Security Management System documentation and understand that you’ve met the requirements, at least in theory! This stage is more of a desktop review of the ISMS with the auditor, covering the mandatory areas and ensuring that the spirit of the standard is being applied. Forward-thinking certification bodies are starting to do these remotely with platforms, like ISMS.online, which drives down cost and can speed up the process too. The outcome from this exercise is a recommendation for Stage 2 audit readiness (perhaps with observations to reassess during the Stage 2 audit) or a need to address any non-conformities identified before further progress can happen.
What is the Stage 2 Audit for ISO 27001?
Having completed the Stage 1 Audit, the auditor has a basic understanding of your organisation, its information security posture and its approach to information security management. They will now want to see that you actually DO what you say you are doing. Furthermore, they will expect to see that you are assessing how effective your ISMS is and how you manage continual improvement. The aim of the Stage 2 Audit is to prove that your ISMS is operating as described, in accordance with the requirements of the standard and is delivering the level of information security judged to be adequate and proportionate to the risks your organisation faces. Stage 1 is quite straightforward but Stage 2 is all about giving the auditor that confidence you are demonstrating that ISMS in a living breathing form across your stated scope.
As a final cross-check prior to the Stage 2 Audit, ask yourself these simple questions:
- Have we closed any critical findings from the Stage 1 Audit?
- Can we evidence the operation of all required ISMS processes?
- Are objectives being measured and met?
- Is the risk register being maintained?
- Is security awareness and training deployed to those in scope?
- Are competency gaps being closed?
- Are Internal Audits being conducted?
- Are Formal ISMS Management Reviews being conducted?
- Are corrective actions and improvements being logged & tracked?
- Can we evidence the operation of all relevant information security controls & processes?
- Can we show that where incidents are identified, these are being logged, tracked, managed and implemented over time?
- Can we show that we are happy with our current risk profile? That is:
- A risk is tolerable with no further action necessary at this time
- A risk is currently tolerable when considering identified improvements that have been logged and are being implemented over a defined timeframe?
If you can answer “yes” to these questions, then you are probably ready for the Stage 2 Audit.
The auditor will investigate further, then sample test your approach and almost certainly select staff to demonstrate they are trained, aware and compliant. It is very important that your staff and other people in the scope (e.g. suppliers) are able to demonstrate they understand where to find and are following your stated policies and procedures if asked by the auditor. ISMS.online offers Policy Packs for compliance demonstration and ISMS communications groups to engage staff and key suppliers on the topic of information security. The sampling of evidence may include:
- Physical inspections (e.g. site/office walk-around)
- Interviews with personnel with responsibility for the ISMS or Information Security
- Interviews with general personnel (e.g. to check awareness)
- Inspection of logs and records (of all types)
- Review of technical controls implementation (e.g. configuration files)
If your scope encompasses multiple locations, the certification body will wish to audit a number of those, especially sites with any key functionality. They will provide exact details when you request your quotation from them.
There are two outcomes from the Stage 2 Audit:
- Not recommended for certification – This is highly unusual as any major problems should have been identified during the Stage 1 Audit. It does happen if actions to address non-conformities from the Stage 1 Audit have not been taken. Very occasionally a previously undiscovered major non-conformity will be found. If this does happen, then the certification body will almost certainly stop the audit immediately and will detail the steps required to close the issue. In the worst case, a re-run of the Stage 2 Audit may be necessary.
- Recommended for certification – This means that subject to peer-review of the audit within the certification body and potential review by the accreditation body (e.g. UKAS) you will receive your certification.
You may also receive areas for improvement or minor non-conformities that should be addressed in accordance with the auditor recommendations.
What happens after the ISO 27001 Stage 2 Audit?
If you have been recommended for certification… CONGRATULATIONS! Enjoy the moment as it is really hard work building an independently certified information security management that people can trust. If it was simple everyone would do it but they don’t. Whilst ISMS.online makes the whole journey much easier and faster it is still a wonderful achievement worth celebrating.
The certification body will then peer-review the audit report internally and pass the report to the accreditation body (e.g. UKAS) who look at a sample from each certification body to ensure standards are maintained. Once the accreditation body gives their seal of approval a certificate will be issued. The process of review and certification issue normally takes 3-4 weeks. The certificate lasts for 3 years and you’ll have surveillance audits at regular intervals on the way, usually annually.
For now, you can move on by “celebrating and building on success” as an ISMS is for life, not just the first certification. What can be given can easily be taken away if you don’t maintain and improve your approach over time so remember to keep doing a little, often, and you will find it quickly integrates into a very manageable, positive experience for you and the organisation.







