
ISO 27001 is an International Standard for Information Security Management Systems (ISMS).
It is based on the principle that effective management systems must include appropriate control measures to protect information assets against loss, damage, unauthorised disclosure, misuse, unauthorised access, modification, and destruction.
In short, ISO 27001 is a set of standards for managing risk related to information security. It covers policies, procedures, training, monitoring, auditing, incident response, and communications.
This guide provides an overview of ISO 27001, explaining what it is, why organisations use it, how to implement it, and how to maintain compliance.
Cyber attacks are increasing yearly, and many people don’t realise how much damage they can cause. One study found that $1 trillion worth of damage was caused by cybercrime in 2016 alone.
The purpose of ISO 27001 is to guide how to manage risks associated with information assets within organisations. This includes ensuring that the organisation meets its legal obligations, such as data protection, privacy, and management of publications.
The ISO 27001 standard is designed to help businesses manage risk and improve information security across their entire organisation. It includes requirements for managing information about people, processes, technology and physical assets. It covers incident response, training, internal audits, management, and monitoring.
ISO 27001 includes guidance on how organisations must manage risks associated with information assets. The standard is intended to help organisations better understand what constitutes a threat to confidentiality, integrity, availability, and accountability. It defines these threats and outlines ways organisations can mitigate them.
The ISO 27001 international standard provides requirements for practising efficient information security and ensuring it is appropriately used. This includes providing access control, managing risk, monitoring activities, ensuring privacy, and maintaining confidentiality.
Organisations can use it to assess whether they meet key criteria such as having a documented threat assessment process, implementing robust access control processes, providing adequate training and awareness programs and maintaining accurate records of activities.
Companies that comply with the information security standard, ISO 27001 will be seen as more credible and trustworthy. A lack of compliance could lead you to fines or even prosecution under UK law.
An effective ISMS helps ensure an organisation’s information’s confidentiality, integrity, availability, and authenticity. Implementing an ISO 27001 compliant ISMS requires careful planning; the benefits are worth the investment. Your business can differentiate itself from competitors by complying with industry best practices worldwide.
An ISO 27001 certification demonstrates that your organisation complicates with international standards. There are many benefits to achieving an ISO 27001 certification, including:
Organisations wishing to explore information security management systems may have come across both ISO 27001 and 27002 standards.
ISO 27002 focuses specifically on guidance regarding controls found in ISO 27001. It addresses the same topics as ISO 27001 but includes additional ones such as physical and logical access control, authentication, authorisation, encryption, and segregation of duties.
ISO 27001 is the primary standard in the 27000 family. Companies can get certified against ISO 27001. However, they cannot certify against ISO 27002:2022 since it is a supporting standard/code of practice.
ISO 27001 Annex A, for example, provides a list of security controls but does not tell you how to implement them; instead references ISO 27002.
ISO 27002 conversely provides guidance on implementing controls used in ISO 27001. The great thing about ISO 27002 is that the controls which it discusses are not mandatory; companies can decide whether they want to use them or not, depending on if they’re applicable in the first place.
ISO 27001 certification is one of the most important certifications for businesses today. This international standard covers how organisations protect sensitive customer information.
Having ISO 27001 certification will help you build credibility and trust within your industry. Your customers will see you as a leader in cybersecurity and feel safer doing business with you.
Companies that are ISO 27001 Certified have a competitive edge over those that aren’t because they demonstrate that they care about protecting personal information. They show that they understand privacy and how to implement policies and procedures to ensure no unauthorised access occurs. And if there is ever a security breach, they’ll have a system to notify affected individuals quickly and efficiently.
A company can go for ISO Certification by inviting an accreditation Body to perform the audit and, if the Auditors find the company compliant, to issue the ISO Certificate.
There are three phases to achieving ISO 27001 certification. Phase one includes a self-assessment questionnaire that determines whether or not an organisation needs to take further action. If it does, phase two involves conducting a full-scale audit of the organisation’s entire system. Finally, phase three consists of a yearly re-audit to ensure that everything is still up to date and compliant.
A gap analysis audit is conducted to help identify potential problems ahead of the official certification audit. During this process, a team of experts reviews the organisation’s policies, procedures, processes and practices to see what gaps exist. These gaps could lead to future issues or even allow attackers to access sensitive data through data breaches.
Companies are given a stamp of approval once they demonstrate that they have met specific requirements. These include implementing policies and procedures to prevent unauthorised access to confidential information, training employees about those policies and procedures, monitoring employee activity to ensure adherence to policy, documenting processes and strategies, and regularly testing systems to ensure they’re still working correctly.
ISO 27001 certification can be a challenge for many businesses. Getting certification involves a lot of hard work, which can eat into your time and resources.
ISMS.online helps you get certified faster, easier and cheaper. You can manage your certification project 100% online. You can build your entire ISMS system online to achieve certification and automate your ISO 27001 certification project.

Book a tailored hands-on session
based on your needs and goals
Book your demo
The benefits of ISO 27001 certification go beyond ensuring that your organisation’s data is protected. You’ll see a difference in your bottom line too. Customers trust certified companies more and tend to spend more money with them. So if you want to build a reputation for yourself as a trustworthy company, ISO 27001 certification is the way to do it.
ISO 27001 re-certification is integral to keeping up with information security best practices. To keep your ISO 27001 certification active, you must re-certify every three years.
ISO 27001 specifies that an organisation needs to conduct audits every three years to verify that the policies and procedures remain effective.
Your company should regularly review its internal policies and procedures to ensure they are still relevant and up-to-date.
Regular internal audits ensure that your information security programs are still working effectively. If your processes are out of date, you should update them.
In addition, ISO 27001 recommends that organisations adopt a yearly third-party audit to determine if they are meeting their goals.
These annual surveillance audits are required to maintain ISO 27001 certification. They involve reviewing documentation and interviewing employees to determine if any changes need to be addressed.
This ensures that your organisation continues to meet the requirements of the standard.
A successful ISMS is an ongoing process. You need to update your ISMS regularly to meet changing compliance obligations and business needs. ISMS.online makes it easy to maintain and update your ISMS to meet changing regulations, threats and vulnerabilities.
Automated ISMS updates mean you can spend less time managing your ISMS and more time on what’s important – running your business.
ISO 27001 requires that a written policy address confidentiality, integrity, availability, accountability, privacy, and regulatory requirements. Additionally, the policy must define responsibilities and accountabilities within each function.
Another important aspect of ISO 27001 includes a management system life cycle (ISMS). This helps ensure that an organisation implements changes over time-based on experience and feedback.
Your organisation must document its privacy and confidentiality policies and procedures. Those policies and procedures must cover topics such as employee responsibilities, physical access control, network security, email usage, backup procedures, retention schedules, and destruction of documents.
Employees must undergo training on how to handle sensitive information. They must understand the importance of keeping customer data secure and know how to implement appropriate safeguards.
ISMS.online includes everything you need for ISO 27001 compliance. Whether it’s policy templates or risk assessments, you’ll be able to build a complete ISMS and generate reports instantly.
The ISO 27001 standard provides guidance and requirements for establishing and managing an effective information security program. The standard is intended to help organisations implement appropriate policies and procedures to protect against threats to confidentiality, integrity, availability, and unauthorised disclosure.
A good ISMS helps ensure that your organisation meets its legal obligations and protects against data loss, theft, unauthorised access and misuse. However, choosing the wrong certification body could mean spending money on unnecessary training courses, expensive audits and wasted resources.
ISMS.online takes the guesswork out of meeting ISO 27001 requirements. Our platform gives you everything you need to manage your ISMS so that you can focus on doing meaningful work instead getting overloaded with spreadsheets and unnecessary paperwork.

Book a tailored hands-on session
based on your needs and goals
Book your demo
There are many clauses and controls in the ISO 27001 standard, but they are not mandatory. You do not need to follow every single rule in the standard to achieve ISO 27001 certification. However, it is impossible to comply with the standard without following every clause.
ISO 27001 compliance requires organisations to implement physical controls such as firewalls, intrusion detection systems, antivirus software, network monitoring tools, etc.
Organisations should consider implementing physical security control to ensure compliance with international standards such as ISO 27001. This will help organisations to comply with the requirements of the law and regulations.
The benefits of implementing physical security controls are many. For instance, it helps organisations to detect threats early and take action to mitigate risks. In addition, it protects data from unauthorised access, modification, deletion, or disclosure.
Technical controls are “procedures, policies, standards, specifications, guidelines, protocols, processes, and practices used to ensure that information technology systems meet specified requirements.”
This includes protecting data against unauthorised access, modification, destruction, or disclosure. These controls include all the hardware and software installed on an organisation’s premises. They include firewalls, intrusion detection systems, antivirus software, anti-spyware software, etc.
Organisational controls are “the actions an individual or group takes to prevent, detect, correct, respond to, or report incidents involving the use of information technology.” Examples include:
These are typically the most common form of controls because they involve the creation of policies and procedures to govern how employees perform their jobs. They are often seen as part of a more extensive governance program.
These are the second most common control method, ensuring that workflows are followed correctly. For example, you might require that certain documents be signed before being submitted to management.
Human resource controls are an essential component of any organisation’s information security program. They help prevent data loss or unauthorised access and ensure compliance with federal laws such as HIPAA, Sarbanes-Oxley, and others. In addition, they provide visibility into how employees use corporate assets. Knowing whether you comply with those regulations without proper controls is difficult.
Legal controls are a set of agreements to manage the relationships between different parties. They are used to ensure everyone follows the same rules and procedures. Legal controls help avoid problems down the road because they set expectations about how things will work. For example, you might use legal control to establish how many times a person can call you each week or what percentage of revenue must be paid.

Book a tailored hands-on session
based on your needs and goals
Book your demo
According to the ISO 27001 framework, organisations must establish a documented process for assessing risks and vulnerabilities; develop plans for mitigating those risks; implement controls to prevent unauthorised access, use, disclosure, modification, alteration, or destruction of data; monitor and report incidents; and conduct regular risk assessments.
Companies must document what they know and how they plan to secure themselves against cyber threats. They must also provide proof that they have implemented controls to mitigate risks and ensure compliance. Finally, they must demonstrate that they regularly assess risks and maintain control over sensitive data.
An ISO 27001 audit will look at whether or not the documentation includes the necessary elements outlined above. If it does not, the auditor will recommend changes to ensure the system complies with the standard.

Download your free guide to fast and sustainable certification

We just need a few details so that we can email you your guide to achieving ISO 27001 first-time
Download your free guide now and if you have any questions at all then Book a Demo or Contact Us. We’ll be happy to help.
If you don’t use ISMS.online, you’re making your life more difficult than it needs to be!
The best way to start implementing an information security management system is to begin with a clear understanding of what it is you want to accomplish. This includes defining the scope of the project and establishing goals. Once you know where you are starting from and where you want to go, you can determine how much work needs to be done to reach those goals.
An excellent place to start is with an assessment of current practices. What do you already do today? How well does your system support your processes? Do you use a formalised procedure for handling requests? If not, why not? Is there a documented set of rules for access control? Are there policies and procedures in place to ensure data integrity?
Suppose you find that many of your processes are manual or ad hoc, consider automating some. For example, automate the request form if you don’t have a formalised approval process for purchasing equipment. Automation frees up resources to focus on more critical tasks.
Once you’ve determined the areas that need improvement, you’ll need to decide whether to develop a plan based on a process or a checklist approach. Either case, you’ll need to establish objectives, identify risks, and determine responsibilities. You’ll also need to specify how often you intend to review each item on the list.
Finally, you’ll need to implement the changes you’ve identified. Start small and build momentum. Document everything, including training materials, checklists, and reminders.
The process of defining an information security management system (ISMS) scope is often overlooked. This oversight could lead to problems downstream. Some organisations define their ISMS too narrowly, causing it to fail.
The European Union General Data Protection Regulation (EU GDPR) went into effect on May 25th 2018. This regulation requires organisations to perform a risk analysis before implementing an ISMS. Organisations are required to assess risks associated with data collection, storage, processing, transmission, access, use, disclosure, loss, damage, theft, unavailability, unauthorised modification, and unlawful destruction of personal data. Failure to do so could lead to fines up to 4% of global revenue or 20 million euros per violation.
A risk assessment is a team reviewing the current state of IT assets, processes, procedures, policies, and practices. A risk assessment allows companies to identify threats to their systems and take appropriate measures to mitigate them. Identifying risks helps organisations understand what needs to change to ensure compliance with the law.
ISMS.online helps with information security risk management, minimise disruption and maximise efficiency across your entire organisation. Our software is easy to use and includes all the features you need to manage information security aspects in your organisation. And you can save time and money by using our web-based system to deliver all your documentation requirements in one system.
Your statement of applicability must cover all relevant aspects of your organisation.
You should explain why any Annex A controls are excluded and be sure to provide a rationale behind each exclusion.
Information security policy documentation is crucial because it helps you communicate what your organisation stands for within the industry. A well-written document will help you build trust with stakeholders and demonstrate how you plan to protect sensitive data.
If your organisation doesn’t have an existing information security policy, start by documenting your current practices. This will give you a baseline against which you can measure future improvements.

Download your free guide
to streamlining your Infosec
The operationalisation of an information security management system (ISMS) is critical to ensuring that it meets the entire organisation’s needs. This includes ensuring that the processes, policies, and controls governing how data is handled are consistent throughout the enterprise.
In addition, an ISMS must be aligned with the organisation’s overall strategy. For example, you might want to ensure that your ISMS addresses cyber security threats like cybercrime and phishing attacks. You could also use the ISMS to manage regulatory requirements. Finally, you might want to ensure that your ISMS addresses internal risks such as insider threats, data loss, intellectual property theft, etc.
ISMS.online helps you implement a comprehensive management system tailored to your business needs. Our platform will help you meet compliance obligations and embed the very nature of information security into your organisations culture at less cost to your business.
An internal audit should be performed every year or two. This type of audit helps you assess how well your processes work, what risks, and what control measures are used. When performing an internal audit, it is important to conduct a risk assessment, map out the current processes, identify gaps, and find ways to improve the existing system.
From generating test plans to helping you identify remediation activities, ISMS.online puts the tools at your fingertips when you need them most and helps your organisation achieve its strategic objectives.
Internal auditors are there to help you make sure your business is running smoothly. They do this by performing regular internal audits. These audits help you identify potential problems before they become big ones. However, it isn’t enough to simply perform audits; you must implement corrective actions once you’ve identified the problem. If you don’t, your business could suffer serious consequences.
The most common reason businesses fail to address problems found in audits is that they lack the proper tools to do so. In many cases, a simple spreadsheet won’t cut it. You’ll need something more robust to ensure you’re following up on every issue uncovered in an audit. For example, you might use a tool like Salesforce to track sales leads and follow up on each. This way, you know exactly how many people you’ve reached out to and whether those contacts turned into customers.
Once you’ve implemented corrective actions, you’ll want to get feedback from your team members to see if you’re doing things correctly. Your employees should feel comfortable giving honest feedback to management. Having open lines of communication helps everyone work together toward the same goal.
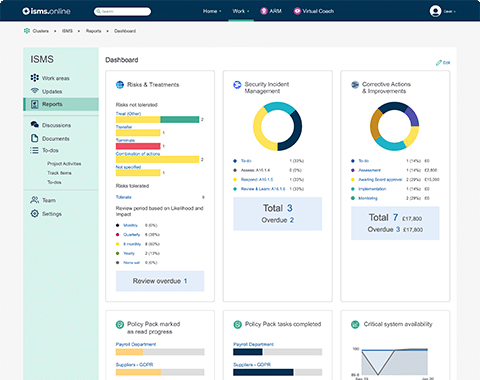
Automated reporting within ISMS.online helps you ensure compliance. Receive simple reports in just one click detailing the status of submitted evidence, and assign action items as required, all from a single dashboard.
A consultant will support your ISO 27001 certification journey, including training and implementation. This could include helping you choose the right solution, providing guidance during the assessment, and keeping you through the certification process.
Consultants are experts in their field and can offer advice about choosing the best solution for your organisation, such as whether it makes sense to go for a commercial product or a DIY approach. They can also advise you on how to implement the chosen solution.
Having a certified consultant helps you ensure that everything goes smoothly. If there are any issues, consultants can resolve them quickly and efficiently.
Choosing the suitable ISO Certification Body makes implementing a successful information security management system (ISMS) easier, whether you want to comply with international regulations such as ISO 27002 or improve your customer confidence.
Check the credentials of the certification body itself. Look up their address, telephone number, email addresses and web presence. Ask around for recommendations. Make sure you talk to people who have used the firm before. Also, take note of any complaints lodged against the company.
ISMS.online is an end-to-end information security and privacy risk management platform helping companies effectively manage risk throughout the life-cycle of data.
After on-boarding and gaining hands-on experience using our platform, you will have all the controls and steps required to become ISO 27001 certified.
ISO 27001 may be complex, but ISMS.online makes it simple for you. Step-by-step guidance informed support tools and automated workflows ensure that you understand your obligations quickly, your compliance efforts stay on track and gives your organisation an competitive advantage.
Book a tailored hands-on session based on your needs and goals.
100% of our users achieve ISO 27001 certification first time