Demystifying Risk Assessment: Starting with Controls for ISO 27001
Table Of Contents:
Risk Assessment in Information Security
Risk management plays a vital role in any organisation’s information security posture. A proactive approach to identifying, evaluating, and determining the treatment for potential risks allows you to mitigate risk more effectively, better manage outcomes, and reduce the impact of information security incidents on your business should they occur.
Good risk assessment and management practice is mandatory for anyone seeking to comply with the ISO 27001 standard. The standard requires your organisation to establish and maintain information security risk assessment processes, including risk acceptance and assessment criteria to measure the likelihood and impact of risks.
Risk management in ISO 27001 aligns directly with the standard’s information security controls, which can be implemented to treat your identified risks.
Effective Risk Assessment in ISO 27001
As part of ISO 27001 compliance, your organisation should develop a risk assessment and treatment process. Risk assessments should be conducted regularly to ensure you consistently identify and address new risks, and risks should be assigned to risk owners for the duration of their lifespan.
There are several key terms used to classify and understand risk:
- Risk: the potential for destruction, damage or loss of data or assets
- Threat: a person or action that increases the chances of an incident, such as a threat actor sending phishing emails to employees or exploiting a vulnerability
- Vulnerability: a weakness in your organisation’s applications, networks or infrastructure that could expose your data and assets.
Risk Identification
Before identifying risk, you should determine the information assets your organisation needs to safeguard by creating an asset register. Assets include:
- Information or data
- Intellectual property
- Physical locations and buildings
- Systems
- Hardware
- Software.
When identifying risks to these assets, you should consider risks that may impact data confidentiality, integrity, and availability (known as CIA), including:
- Any external or internal issues (in line with Clause 4.1)
- The needs and expectations of interested parties (in line with Clause 4.2)
- Applicable legislation, regulations, or contractual requirements
- The scope of the system (in line with Clause 4.3)
- Any additional compliance regimes within the organisation, such as Cyber Essentials.
Risk Analysis
Risk analysis is the process of scoring each risk based on the likelihood and impact of occurrence.
Within the ISMS.online platform, you can score the likelihood of risk from very low to very high (1-5) and the impact from none to severe (0-5). These factors score each risk out of 25, with impact being considered more important than likelihood. This allows you to prioritise treatment based on the risk score.
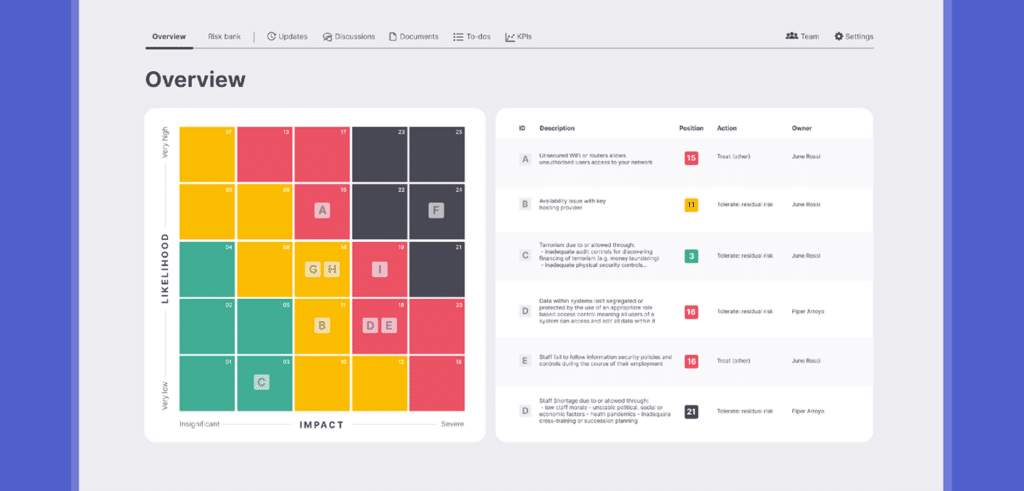
For example, your organisation might identify an email being misdirected to the wrong recipient by an employee as a risk. Measuring against your criteria, you may decide that the likelihood is medium and the impact is minor due to the possibility of commercial information being mistakenly sent to many recipients compared to a single recipient, giving the risk a relatively low score. The next step is to decide how to treat that risk.
Risk Treatment
Each risk’s owner is responsible for identifying the appropriate risk treatment. They should also consider criteria for tolerating the risk. The five treatment options are:
- Terminate – to remove the risk entirely
- Treat – to reduce the risk impact or likelihood
- Transfer – transferring or sharing the risk (e.g. by acquiring insurance)
- Tolerate – to accept the residual risk
- A combination – taking more than one of the actions above.
Risk acceptance, also known as risk tolerance, should be based on the following criteria:
- The level of risk to be accepted
- The type and volume of personally identifiable information (PII) at risk
- Legal, regulatory or contractual obligations
- Business objectives and compliance requirements
- Any other conflicting risks that may be introduced or changed from treating the identified risk, such as risks to resourcing levels.
You may decide to tolerate the example risk after considering further context. For example, your organisation may have implemented broader controls that reduce the impact of an email being mistakenly forwarded to the wrong recipient, such as Annex A.5.14 information transfer and A.6.4 disciplinary process.
Treatment may be required for more severe risks, such as a personal data breach. In this example, the risk owner may treat the risk by regularly running phishing awareness training for all employees and deploying tools to monitor phishing activity. The level of risk also indicates how often it should be reviewed—for example, monthly, quarterly, six-monthly, or annually.
Addressing Risk with ISO 27001 Controls
Your risk assessment process will leave you with a clear set of risks, while the risk treatment process requires you to select appropriate risk treatment options and determine the controls you need to implement. ISO 27001:2022 Annex A provides a set of 93 controls in four categories: organisational controls, physical controls, people controls and technological controls.
These controls include processes, policies, devices, practices, and other conditions or actions that maintain or modify risk, such as password policies, antivirus software, and cryptography. Implementing them helps mitigate risks and reduce the impact of information security incidents. Using the controls laid out in ISO 27001:2022 Annex A ensures you’ve taken an exhaustive approach to addressing risks to your business.
Essential ISO 27001:2022 Annex A controls include:
- A.5.1 Policies for information security, which requires your organisation to have an information security policy document in place to protect against information security threats
- A.5.34 Privacy and protection of PII, a preventive control with guidelines and procedures to help your organisation fulfil its requirements relating to the storage, privacy and security of personally identifiable information (PII)
- A.6.8 Information security event reporting, which aims to facilitate timely, consistent and effective reporting of information security events detected by personnel
- A.7.9 Security of assets off-premises, which requires organisations to set up and implement protocols and regulations that cover all devices owned or used on behalf of the company
- A.8.7 Protection against malware, which provides guidelines for executing a malware defence encompassing controlled systems and account access, change management, anti-malware software and organisational information security awareness
- A.8.24 Use of cryptography stipulates seven requirements organisations must abide by when using cryptographic methods.
The risk and control identification processes are simplified within the ISMS.online platform. As standard, the platform identifies over 100 common risks and suggests relevant controls that can be applied to treat each risk, significantly reducing your risk assessment and management workload.
The Importance of Ongoing Risk Monitoring
Continuous monitoring and reviews are a vital part of risk management because a risk’s likelihood or impact may change over time, meaning a new method of treatment is required. For low-level risks, you may decide that annual reviews are sufficient, while medium-level risks may need to be reassessed every three or six months and high-level risks every month.
Whatever review period you decide is appropriate for an identified risk, it’s vital to ensure that risk owners deliver it so that you have an up-to-date view of your organisation’s risk mapping. The ISMS.online platform automatically notifies risk owners when events such as annual risk reviews are due, ensuring that your risk management is robust and consistent with minimal effort from your team.
These regular reviews can be used as evidence that your organisation maintains and develops a robust information security management system (ISMS) for your auditor.
Simplifying Risk Management with ISMS.online
As well as providing a ready-made risk bank with over 100 common business risks, the ISMS.online platform also contains a dynamic risk map. The map gives you an up-to-date oversight of your organisation’s risk profile, so it’s easier than ever to coordinate your risk management, view potential threats and opportunities, and keep stakeholders informed.
The platform also comes with a dynamic reminders feature, which automatically reminds risk owners when it’s time to review a risk they’re responsible for, whether it needs to be reviewed monthly, quarterly, six-monthly, or annually. The risk history graph enables you to identify and track risk sources and highlights how your risk profile has evolved.
Proactively Manage Your Information Security Risk
For many businesses, ISO 27001 certification presents an undeniable competitive advantage: they can prove to customers and prospects that they’re committed to keeping their data safe.
Risk management and control implementation are vital aspects of ISO 27001 certification, forming the core of a robust information security posture and ISMS. Proactive risk management allows you to monitor risks, prevent incidents and reduce the impact of incidents that do occur. By prioritising risk assessment as a continuous process, you can ensure your organisation is always prepared to respond to the latest threats.
The ISMS.online platform provides a simplified approach to risk assessment, with a risk bank, suggested controls for each risk, and automation that reminds risk owners when it’s time to review the risks they’re responsible for. If you’re ready to achieve ISO 27001 compliance easily and save time on your risk management, book your demo.