CISA’s Updated Zero-Trust Model
Zero trust might have once been just an analyst buzzword, but it now has the official U.S. government stamp of approval. The Cybersecurity & Infrastructure Security Agency (CISA) has released the second version of a guide to implementing this security model. It promises to be more than just shelfware because federal agencies have been ordered to adopt zero-trust principles with tight deadlines.
What is Zero Trust?
While the term ‘zero trust’ has garnered a lot of press lately, the underlying concepts are well-established. The phrase first cropped up in the IT sector outside niche circles in 2010 as part of a Forrester Research report. However, the ideas it represents – the need to verify everything in an untrustworthy environment – date back far earlier.
The Open Group’s Jericho Forum heralded the erosion of the traditional network perimeter in 2004, calling it deperimeterization. As companies exchanged data with business partners and located more of their assets outside the core company network, it became more challenging to trust whoever or whatever tried to connect mindlessly. Instead of the old citadel model, where the network had an impermeable hard outer wall, IT infrastructures had become more like a set of encampments, each housing some assets and needing its own protection.
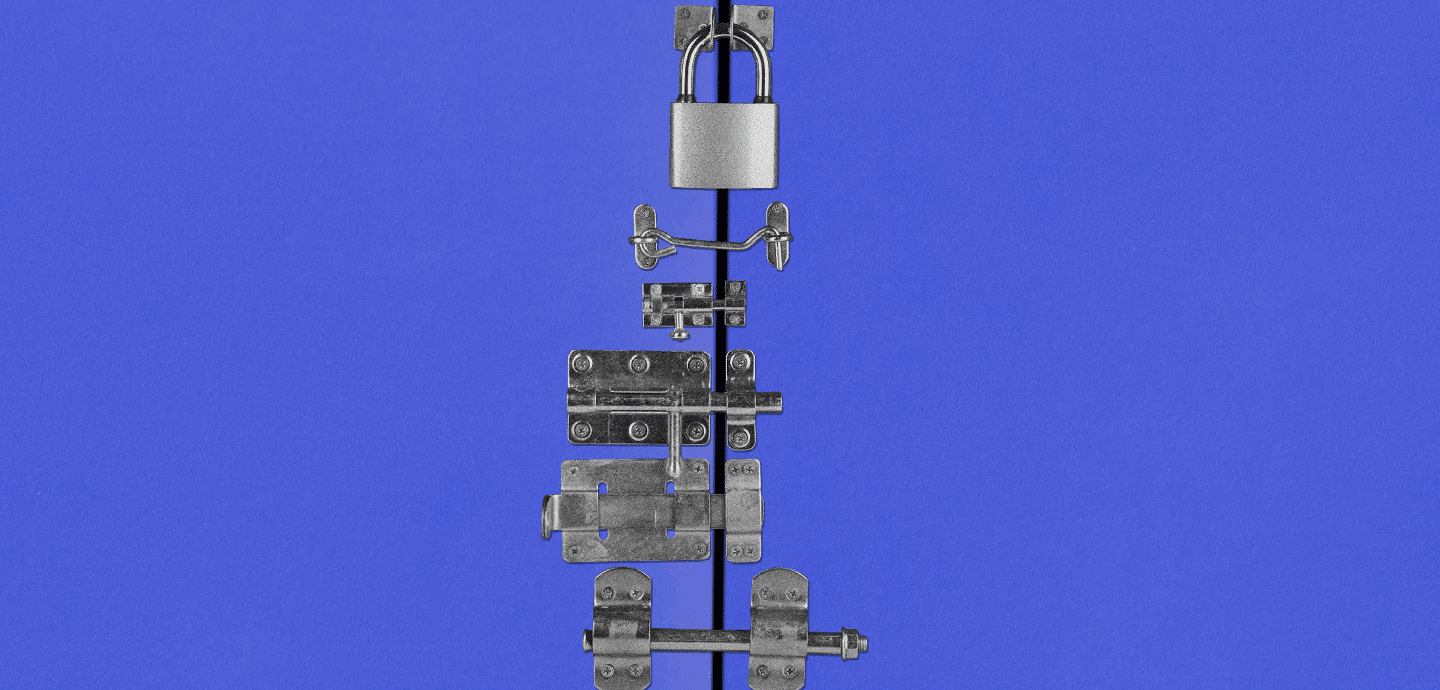
This changed the way that IT systems authenticated people. Back in the day, if you had the credentials to get onto the network, you were trusted and could go anywhere. Zero trust abandons that idea. Instead, there is no one barrier to get past. Every digital door in the place is padlocked, and you must have some kind of key.
The White House Buys In
The U.S. government has bought into the zero-trust concept, first advocating for it through Executive Order 14028 in May 2021. The following January saw it follow up with mandates for zero trust. These came in the form of National Security Memorandum 8 (NSM-8), which instructed its use in the national security community, and the MS-22-09 memo from the Office of Management and Budget. The latter directed federal agencies to implement zero-trust measures by the end of next year.
CISA, the Department of Homeland Security agency that handles the cybersecurity side of the domestic security effort guides federal organizations and the private sector in issues like this. It dutifully published its Zero-Trust Maturity Model in September 2021, as directed by the Executive Order. This document was intended to help agencies transition to the new model.
The Agency released an update to this guide in April this year following a public consultation period. The most significant change in the second version is the addition of another maturity stage in an organization’s journey to zero-trust nirvana.
There were originally three stages: Traditional, Advanced, and Optimal. Traditional was effectively business-as-usual, with practically no cohesive zero-trust implementation at all.
Companies at the Traditional level that had done any work at all on zero trust had kept it to a narrow scope. The maturity model outlines five pillars to divide up the work of implementing zero trust, indicating the breadth of change required. These pillars are Identity, Devices, Networks, Applications and Workloads, and Data. Companies at the Traditional level focused on zero trust work on a per-pillar level rather than taking a more cohesive approach.
The maturity model outlines three ‘cross-cutting’ capabilities that extend across each of these pillars to help federal agencies and private-sector institutions address zero-trust needs more broadly. These three areas are Visibility and Analytics, Automation and Orchestration, and Governance.
Commentary on the first version of the guide argued that the jump between Traditional and Advanced was too significant. Instead, they asked for an additional stage that would bridge the two. CISA responded by adding an Initial stage after Traditional. It also adjusted the language for the other more advanced stages across the five pillars to accommodate the extra maturity level.
Companies at the Initial stage are just beginning to automate tasks like assigning attributes and configuring life cycles, the revised guide says. At this point, they’re starting to get to grips with policy decisions and enforcement. Other tasks just getting underway cover the concept of least privilege and gaining some form of cohesive visibility across internal systems.
Unsurprisingly, people asked for an extra step in the zero-trust maturity process. This new cybersecurity mindset represents such a broad change to how we handle enterprise access and authentication that no vendor or product can do it all. It’s more of a discipline than a product category, involving changes across the entire infrastructure and significant updates to policy. For many organizations, it will be a slow burn, more like lighting a thousand candles than flipping a single switch, and this extra step gives them a more straightforward place to begin. Making the on-ramp a little shallower will be a welcome change to the road map for many.



