
An essential element of GDPR is to preempt risk to the security of personal data. A Privacy Impact Assessment (PIA) is the process which helps organisations to identify and mitigate the risks of any potential new project.
Choosing to begin a Privacy Impact Assessment (PIA) is normally triggered by the planning of a new project. This is because it can give you the opportunity to analyse how the new project is likely to affect your customer’s, client’s or staff’s privacy.
According to the Information Commissioner‘s Office:
‘Conducting a PIA does not have to be complex or time consuming but there must be a level of rigour in proportion to the privacy risks arising.’
So you have established that you need to conduct a PIA, but where do you start? Before you do anything, it’s important to ensure that the PIA is a flexible process that is easily integrated into your organisation’s way of working and planning. You should also begin the PIA in plenty of time. The ICO recommends that you consider the following areas:
Consulting relevant parties throughout the PIA process helps you to stay on the right track. Internal consultations can ensure that stakeholders and staff are as committed to data protection as you are.
When compiling a list of your internal stakeholders, consider those who are likely to be involved in the projects, like engineers and developers, buyers and marketers. You should also include your Data Protection Officer (DPO) if you have one, and the project management team. When consulting external parties, consider those who are going to be affected by the project.

A tailored hands-on session based on your needs and goals
Some of the key considerations are listed below:
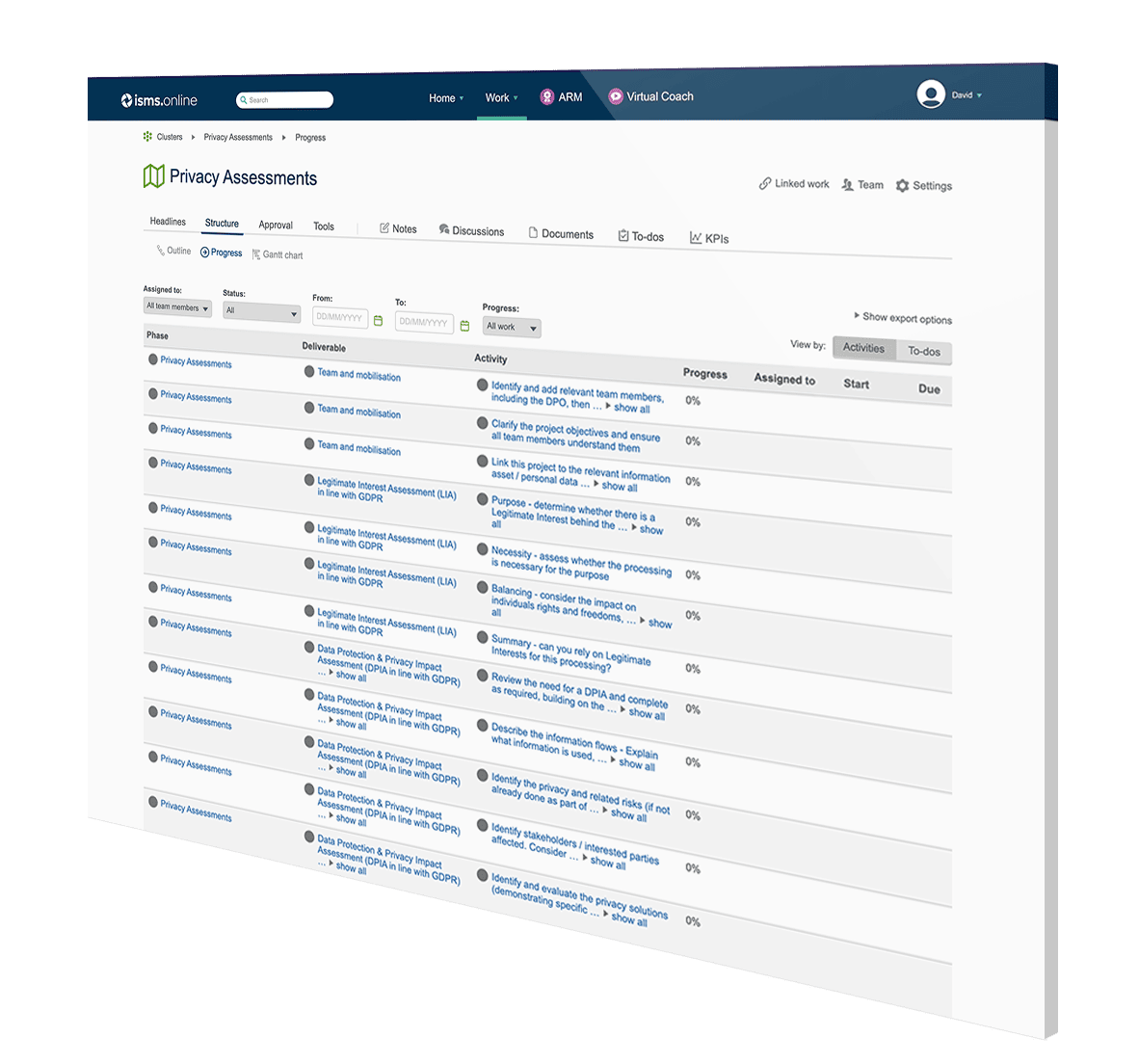
All of this and more is pre-configured in the ISMS.online software for GDPR. You will follow standard and repeatable workflows with team collaboration and approvals. You will have purpose built workspaces to capture all the evidence and link to the wider GDPR compliance project, including the personal data records processing, assets, supplier/processors and risks.
Risk management is taken care of from identification and assessment through to evaluation and treatment.
100% of our users achieve ISO 27001 certification first time