Security Horrors: The NSA and CISA’s List of Top Ten Security Slip-Ups
Table Of Contents:
- 1) Default Configurations Of Software And Applications
- 2) Improper Separation Of User/Administrator Privilege
- 3) Insufficient Internal Network Monitoring
- 4) Lack Of Network Segmentation
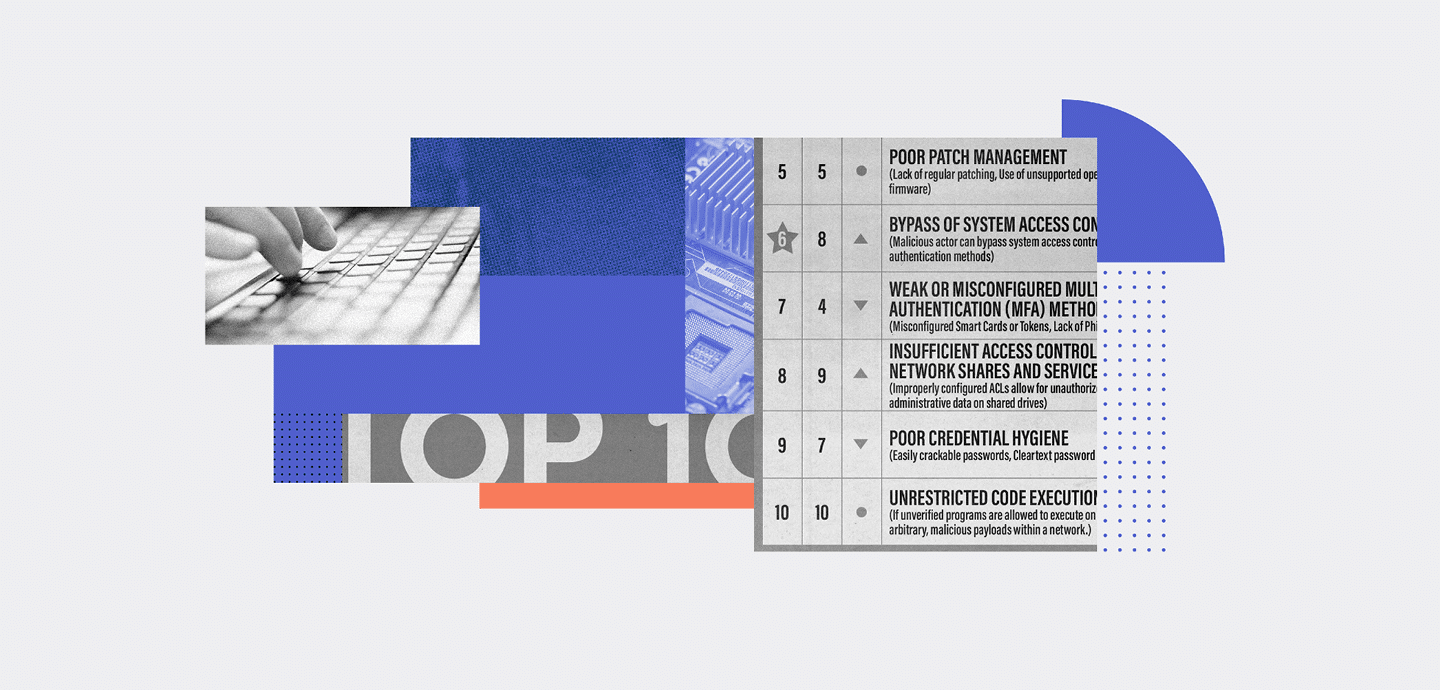
- 5) Poor Patch Management
- 6) Bypass Of System Access Controls
- 7) Weak Or Misconfigured Multi-Factor Authentication (MFA) Methods
- 8) Insufficient Access Control Lists (ACLs) On Network Shares And Services
- 9) Poor Credential Hygiene
- 10) Unrestricted Code Execution
- 11) Mitigation Steps
An insecure network is a cybersecurity defender’s worst nightmare and an attacker’s dream. A single misconfiguration can leave a gaping hole in a network. Yet whether through ignorance, distraction, not enough admins or too many, these misconfigurations are rife. The U.S. National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) see so many of the same ones cropping up that they released a report detailing the ten most common. We’ve lined them up here, along with a discussion of their potential effects and possible mitigation measures.
Default Configurations Of Software And Applications
This classic security SNAFU involves using default administrative access credentials, which can easily be found online. Not changing them leaves administrative control open to anyone who can reach the access portal.
Default configuration problems extend beyond the use of preset factory logins. Services like Active Directory (featured heavily in the teams’ analyses) come with default privilege settings for different services or leave vulnerable legacy services on by default.
For example, for a long time, Microsoft left Active Directory Link-Local Multicast Name Resolution (LLMNR) on by default, even though this name resolution service heralded from the time when DNS wasn’t as ubiquitous as it is now. That protocol has a security issue that attackers can exploit. Microsoft stated in April 2022 that it would phase that service out in favour of the newer, more secure mDNS.
Improper Separation Of User/Administrator Privilege
Least-privilege access is a fundamental tenet of modern security, yet many admins leave accounts with excessive privileges that attackers can exploit. Service accounts are used to access resources as these often have elevated privileges so that they can access some system resources. They’re a prized asset for attackers.
There are various remedial measures here, including restricting the use of privileged accounts to perform general tasks that could make them vulnerable (such as email access), auditing user accounts, and applying least privilege access. We also liked the idea of disabling administrative accounts and only allowing access to them on request for a set time frame.
Insufficient Internal Network Monitoring
Less experienced attackers can make noise when gaining access to the network and moving around it laterally. Organisations that don’t monitor their networks will miss those signals. In some cases, the teams found some people monitoring host machines while failing to check the network, meaning that they could see an attack’s effect on the server but couldn’t see where it came from.
Lack Of Network Segmentation
Carving up your network into logical segments creates security zones that users can only cross with the correct privileges. It’s the network equivalent of securing entry doors for different parts of the building using badge access. Yet many organisations keep their networks ‘flat’, allowing access to any area from anywhere. According to a congressional report, this failure in the Office of Personnel and Management (OPM) network contributed to its successful breach in 2015.
Poor Patch Management
It’s disappointing but unsurprising that failure to patch applications and operating systems is still a problem for organisations. We know that patching everything on the network can be a heavy lift, but prioritising patches based on proper risk analysis can help to identify the most pressing updates. What’s stunning is that according to the report, the teams “frequently observed” organisations that still hadn’t patched MS08-067 – the 2008 remote code execution vulnerability that allowed Confider to spawn – and MS17-010, which allowed the EternalBlue attack upon which the 2017 WannaCry malware was based.
Bypass Of System Access Controls
Attackers will sometimes bypass traditional system access controls. One technique called ‘pass the hash’ uses stolen hashes of credentials (perhaps from a database published on the dark web) to access authentication systems without using a clear-text password.
Weak Or Misconfigured Multi-Factor Authentication (MFA) Methods
MFA is a valuable layer of protection, but it’s no panacea, especially if implemented incorrectly. Common problems include using SMS-based MFA that is subject to SIM swapping, or ‘push bombing’, where attackers pester people to authenticate access. CISA advises using FIDO/WebAuthn as the gold standard to avoid such attacks. App-based authenticators are the next-best choice.
You may have locked down your service accounts, but what about your network drives? Leaving network shares open to unauthorised accounts provides an oft-exploited way in for attackers. The report says they can use open-source tools or simple system commands to scan available shares.
Poor Credential Hygiene
According to the report, using passwords that are easy to crack or storing them in clear text are both common security slip-ups. Keeping passwords in clear text is an obviously insecure move. Yet, even large companies such as Facebook and GoDaddy have stored passwords this way or in a format easily reversible to clear text. Even passwords that are hashed can be retrieved using password crackers.
Unrestricted Code Execution
The tenth common misconfiguration shared in the list is allowing unverified applications to run on hosts. Phishing attackers will often persuade victims to run unauthorised software on their machines.
The report suggests that lists that only permit specific program signatures can help. However, this can be tricky to implement as legitimate programs often come in multiple versions, creating numerous signatures. The report also mentions using read-only containers and minimal images.
Mitigation Steps
The report lists several mitigations for these risks, many of which should be evident to competent security pros. The fact that the NSA and CISA published separate mitigation steps for network defenders and software manufacturers was laudable. All too often, vendors escape criticism for their own insecure practices.
Manufacturer mitigations suggested in the report included following secure software development guidelines from the beginning. This would help to eliminate the bugs that led to subsequent software patches. Vendors should also ship software that is hardened by default rather than requiring extra work on the customer’s part. We liked the idea of ‘loosening guides’ that show clients how to relax security settings where necessary, along with the risks of doing so. It’s much more difficult to add security controls than relinquishing ones already in place.
Other long-overdue measures include eliminating default passwords. While competent administrators should change these, many don’t. Designing software (not to mention hardware) that doesn’t have them would force custom configuration settings. Another is default support for MFA and mandatory MFA for privileged users.
Providing comprehensive audit logs out of the box would help support network monitoring and detect the bypass of access controls, the report added. Access control lists with minimal necessary privileges might make things a little less convenient for users but will also minimise the risk to the system from hijacked accounts.
Another suggestion is support for code execution controls out of the box in operating systems and applications, which would help avoid running unusual code. We’ve already seen some of this, as with Apple’s warning when running code that isn’t from the app store and Microsoft’s decision to block VBA macros from the internet. There’s plenty of room for more.
It’s disappointing that so many of the common mistakes in this list are hardy perennials. They have all cropped up for years in security breaches and will do so for many more. By offering mitigation steps for customers and vendors alike, the NSA and CISA are at least laying the groundwork for more responsible computing.
Unlocking the Power of Security Frameworks with ISMS.online
Leveraging frameworks like ISO 27001 and NIST provides organisations with proven guidance for building comprehensive security programs.
By adopting the requirements and controls outlined in these frameworks, companies can systematically address risks, protect critical assets, and ensure compliance with relevant regulations. The structured approach of mapping an organisation’s specific needs to established frameworks unlocks the power of industry best practices for information security, providing a strategic path for continuously improving defences in a complex threat landscape.
With the proper application of leading security standards, even small teams can build effective programs that safeguard operations and data. Set up a call with one of our experts today to find out how adopting a security framework could benefit your organisation.



