
Cyber Security Report – Selecting third party suppliers using Cyber Essentials (and beyond)
I’ve been digesting The Culture, Media and Sport Committee recommendations following release of its report on cyber security earlier this week.
An important recommendation has been about the selection of third party suppliers. It has not yet been highlighted by the popular press who have chosen to focus on the other recommendations such as hitting CEO pay packets (which we will look at again another day).
Amongst other things, the report recommended:
All telecommunications companies and on-line retailers, and other cyber-vulnerable organisations, should take steps to ensure that compliance with data protection rules and Cyber Essentials are key criteria when selecting third party suppliers.
We agree with that recommendation and it’s another reinforcement of why we have achieved it ourselves, in addition to our UKAS Accredited ISO 27001: 2013 certification.
Our new Cyber Essentials service is out just at the right time to help others too. We are making the preparation and readiness for Cyber Essentials certification a low cost, in some cases free service, within our new ISMS.Online business.
But is Cyber Essentials, or indeed the ten steps to Cyber Security enough when you think about third party selection for areas with high information security risk? Even if a supplier has a low spend for you, but is accessing or providing services that impact information security, you need to give more careful consideration to that selection process.
Given my heritage in supply chain and partnering activity (and the ten year anniversary of my book Alliance Brand), I thought it might be useful to share some other tips around selection criteria that will help you manage risk and get better results.
In my book, I developed a simple mnemonic to support third party selection called TOPSCORER. It is focused on selection criteria for really important relationships, what some people call partners, alliances etc, not your low value activity. So only invest in this type of selection where you have more significant risk and really recognise the importance of the supply area.
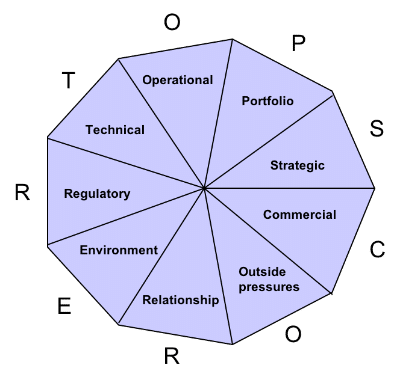
Technical: This is technically why you want the relationship. It is what the supplier or partner prospect brings in terms of core competences and other assets you wish to access. It could include products, services, key resources, IPR, equipment, customers, brand, distribution channel, in-country / local knowledge, capital or other assets.
Operational: This takes into account the supplier’s ability to execute in terms of how it works in practice on the ground with its delivery resources, including its systems, technology and business processes that might need to integrate with the organisation. It also includes its approach to governance, risk management and controls, a key issue for those looking at information security aspects.
Portfolio: There are two aspects to this characteristic; one is the fit of the supplier/partner within your existing portfolio. The second is looking at their portfolio and how your organisation will complement or compete with it and those of its partners/customers/other suppliers.
Strategic: A strong strategic fit and complementary objectives during the life of the relationship is essential if you are considering business critical delivery or serious value adding relationships. Other factors to consider under this characteristic include assessing the complementarity of alliance drivers such as common competitors, similar customer demands as well as a compelling mutual need. Factors that might destroy value should also be considered here such as frequency of changes in direction in the prospect which might signal future competitive threat. An additional consideration is the value and importance that the organisation has in terms of contribution to each other’s strategic goals. A good question to consider is what impact the relationship would have on business if it were terminated suddenly at some future point.
Commercial: Traditional financial attractiveness from a cost/benefit perspective should be considered under this aspect and any upfront ‘skin in the game’ for more intimate collaborations, as it helps signal commitment. The relative sharing of benefits and time to benefit for each party should also be taken into account. The financial health and commercial well being of the party should also be considered.
Outside pressures: Organisations face big challenges by having other priorities or outside pressures competing for management time. Consider potential external distractions such as M&A activity, leadership challenges, other important partners or customers, poor overall partner commercial performance as well as frequently changing staff which might indicate deeper problems inside the prospect. At a personal level, health or family issues can seriously derail key players time and attention so getting to know the people and the organisation is key.
Relationship: Look at the ability to collaborate both organisationally and individually. I deal a lot in my book around this including offering a trust framework. In terms of ability to collaborate, the cultures and practices do not necessarily have to be the same for both organisations, but a strong relationship fit is essential for success. Indeed, sometimes a markedly different performance culture is required for success. For example in shaking up a poor performing business unit, an assertive outsourcing partner might positively improve productivity. Other aspects to consider include comparing leadership styles, values and beliefs, organisational structure and decision making, the way people are managed and motivated, attitude to risk as well as approach to policy and practice from a legal and compliance perspective. If your organisation has a low appetite for information security risk, Cyber Essentials might not be enough. You might also be looking for organisation cultures that complement your appetite, for example where they have already achieved UKAS Accredited ISO 27001: 2013. That would reinforce the other party takes the subject very seriously too.
Environment: Means understanding the impact of the relationship on the specific marketplace in terms of how customers and competitors are likely to react, as well as other interested parties for example market commentators and shareholders. It also encapsulates any relevant aspects around corporate social responsibility and sustainable business impact. It is interesting to see cyber security increasingly becoming part of a quadruple bottom line alongside social, environmental and financial considerations.
Regulatory: Includes broader assessment of macro factors in the regulatory environment facing the area in scope as well as any legal compliance set out for example around industry regulations, anti competitive practices, TUPE and other factors that might need to be addressed with legal safeguards. Data Protection is a key aspect here and that will be growing significantly with EUGDPR. One could argue that the likes of TalkTalk have perhaps been fortunate now with relatively low cost exposure now. The firm could be fined 4% of their global turnover if this had happened after 2018!




