
The National Institute of Standards and Technology (NIST) in the USA has produced a framework to help organisations align their cyber security defence planning and protect the infrastructure from being compromised by the threat of cybercrime.
NIST Cyber Security gives private sector organisations a framework of policies and controls to help prevent attacks from cyber criminals and detect and respond to ones that do gain access.
In the following video, the National Institute of Standards and Technology explains more about the NIST framework’s original aim, the standards, guidelines, and best practices behind it.
We can’t think of any company whose service can hold a candle to ISMS.online.
The National Institute of Standards and Technology is known by its acronym NIST. This is a non-regulatory government agency created to drive innovation and promote industrial competitiveness in science, engineering, and technology.
NIST primary role is to create best practices for organisations and government agencies to follow. The purpose of these security standards is to improve the security posture of government agencies and private businesses that deal with government data.
The NIST Cybersecurity Framework (CSF) is a set of guidelines and best practices designed to help organisations improve their Cybersecurity strategies, which NIST developed.
The framework aims to standardise cybersecurity practices so that organisations can use a single or uniform approach for protection against cyberattacks.
Most organisations aren’t required to follow the NIST compliance, even though it’s recommended for them. US Federal agencies have been required to follow NIST standards since 2017 due to NIST being part of the US Government themselves.
Subcontractors and contractors working with the federal government must follow NIST security standards. If a contractor has a history of NIST non-compliance, they are at risk of being excluded from government contracts in the future.
NIST guidelines can help keep your systems protected from malicious attacks and human error. Following the framework will help your organisation meet the requirements for the Health Insurance Portability and Accountability Act (HIPPA) and the Federal Information Security Management Act (FISMA), which are mandatory regulations.
Organisations lean into NIST compliance as an industry standard due to the benefits it can bring. NIST culture is vital for private companies to promote a better understanding of data handling.
ISMS.online makes setting up and managing your ISMS as easy as it can get.
Both NIST and the International Organization for Standardization (ISO) have industry-leading approaches to information security. The NIST Cybersecurity Framework is more commonly compared to ISO 27001, the specification for an information security management system (ISMS).
Both offer frameworks for managing cybersecurity risk. The NIST CSF framework will be easy to integrate into an organisation that wants to comply with ISO 27001 standards.
The control measures are very similar, the definitions and codes are very similar across frameworks. Both frameworks have a simple vocabulary that allows you to communicate clearly about cybersecurity issues.
Risk maturity, certification, and cost are some of the differences between NIST CSF vs ISO 27001.
If you are in the early stages of developing a cybersecurity risk management plan or trying to mitigate prior failures, the NIST CSF may be the best choice. ISO 27001 is a good choice for mature organisations seeking a more worldwide recognised framework.
ISO 27001 offers certification via third-party audit that can be costly but can enhance your organisation’s reputation as a business that investors can trust – NIST CSF doesn’t offer that kind of certification.
The NIST CSF is available for free, while the ISO 27001 charges for access to their documentation – a start-up company might want to start their cybersecurity risk management program with NIST Cyber Security Framework and then make a bigger investment in the process as they scale with ISO 27001.
I certainly would recommend ISMS.online, it makes setting up and managing your ISMS as easy as it can get.
ISMS.online will save you time and money
Get your quoteWhat is right for your business is dependent on maturity, goals, and specific risk management needs. ISO 27001 is a good choice for mature organisations that face external pressure to certify.
Your organisation may not be ready to invest in an ISO 27001 certification journey yet or maybe at a stage where it would benefit from the clear assessment framework offered by the NIST framework.
The NIST CSF framework can be a strong starting point to your ISO 27001 certification journey as your organisation matures.
Regardless of whether you’re starting with NIST CSF or growing with ISO/IEC 27001, a proactive and efficient information security management system will help you reach organisational compliance.
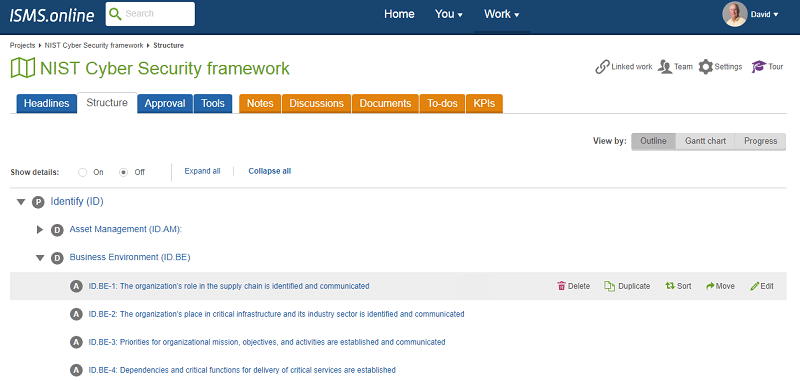
The highest level of abstraction in the framework is the Five Core Functions. They are the foundation of the framework core, and all other elements are organised around them.
Let us take a deeper look at the NIST Cybersecurity Framework’s five functions.
The identify function can help develop an organisational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities.
For betting understanding in a business context, an organisation can focus and prioritise its efforts, consistent with its risk management strategy & business needs, because of the resources that support critical functions and the related cybersecurity risks.
The Protect function outlines suitable safeguards to ensure the delivery of critical infrastructure services. It’s possible to limit or contain the impact of a potential cybersecurity event with the help of the Protect function.
Suitable activities to identify the occurrence of a cyber event are defined by the Detect function. The Detect function allows the timely discovery of cybersecurity events.
Appropriate activities are included in the respond function to take action regarding an identified cybersecurity incident. The respond function helps support the ability to contain the repercussions of a potential cybersecurity incident.
The Recover function identifies activities to maintain resilience plans and restore services affected by a cybersecurity incident. The Recover function helps timely recovery to normal operations to reduce the consequences of a cybersecurity incident.
Following these five functions is advised as best practice as they’re not only applicable to cyber security risk management functions but to risk management as a whole.

Download your free guide
to streamlining your Infosec
We started off using spreadsheets and it was a nightmare. With the ISMS.online solution, all the hard work was made easy.
The degree to which an organisation’s cyber security risk management practices exhibit the characteristics defined in the framework is referred to as the tier.
Tier 1 to tier 4 describes an increasing degree of rigour and how well-integrated cybersecurity risk decisions are into broader risk decisions. The degree to which the organisation shares & receives cybersecurity info from external parties.
Tiers don’t necessarily represent maturity levels; the organisation should decide the desired tier.
Businesses should ensure that the selected level meets organisational goals, reduces cybersecurity risk to levels acceptable to the organisation, and is feasible to implement.
Book a tailored hands-on session based on your needs and goals.
ISMS.online can provide you with a platform to get you on the way to achieving the standard
Each section of NIST Cyber Security is detailed in the secure platform, which makes it easy to follow.
This cuts down on your workload, costs and the stress of not knowing if you have done everything right.
Profiles are an organisation’s special alignment of their requirements and objectives, risk appetite, and resources against their desired outcomes of the framework core.
Profiles can identify opportunities for improving cybersecurity posture by comparing a ‘current’ profile with a ‘target’ profile.
Profiles are used to improve the cybersecurity framework to serve the business best. The framework is voluntary, so there isn’t a right or wrong way to do it.
To create a current-state profile, an organisation must map their cybersecurity requirements, mission objectives, operating methodologies, and current practices. They’ll need to map against the subcategories of the framework core.
The requirements and objectives can be compared against the organisation’s current state to gain an understanding of the gaps.
A prioritised implementation plan can be created through the creation of these profiles and the gap analysis. The priority, size of gap, & estimated cost of corrective actions help plan and budget for improving your organisation’s cybersecurity.
NIST SP 800-53 is known as the National Institute of Standards and Technology Special Publication 800-53, Security and Privacy Controls for Federal Information Systems and Organisation.
It was established to encourage and assist innovation and science by promoting and maintaining a set of industry standards.
NIST SP 800-53 is a set of guidelines & standards that help federal agencies and contractors meet their cybersecurity requirements. Special Publication 800-53 deals with the security controls or safeguards for federal information systems and businesses.
NIST SP 800-171 is a framework that outlines the required security standards and practices for non-federal organisations that handle Controlled Unclassified Information (CUI) on their networks.
First published in June 2015, it included an array of new standards introduced to strengthen cybersecurity resilience in both private and public sectors. Also known as NIST SP 800-171, it went into full effect on the 31st of December, 2017. The latest version, known as “revision 2”, was released in February 2020.
NIST SP 800-207 is a comprehensive publication from the National Institute of Standards and Technology (NIST) that provides guidance on various aspects of cybersecurity. It covers a wide range of topics including the development of a cybersecurity framework, implementation of a Zero Trust Architecture (ZTA), security requirements for cloud computing, security of national security certificates, implementation of an identity proofing process, authentication and lifecycle management for digital identities, and the use of cryptographic controls to protect Personally Identifiable Information (PII).
The document provides detailed steps for creating a cybersecurity framework tailored to an organisation’s specific needs, and guidance on how to implement and maintain it. It outlines the principles and components of a ZTA system, and how to assess the security posture of an organisation. It also provides a set of security controls and best practices for implementing a ZTA system.
In terms of cloud computing, it outlines the security controls and processes that organisations should implement to protect their cloud-based systems and data. It provides guidance on how to assess the security of cloud services and how to develop a cloud security strategy.
The publication also provides guidance on the issuance, management, and use of national security certificates, and the roles and responsibilities of the certificate authorities and the certificate holders. It outlines the requirements for identity proofing, including the use of identity proofing methods, technologies, and services.
Furthermore, it provides guidance on authentication and lifecycle management for digital identities, including the use of multi-factor authentication, risk-based authentication, and federated identity management. It also provides guidance on the use of cryptographic controls to protect PII.
NIST lays out the fundamental protocol for companies to follow when they want to achieve compliance with specific regulations, such as HIPAA and FISMA.
It’s important to remember that complying with NIST isn’t a complete assurance that your data is secure. NIST tells companies to inventory their cyber assets using a value-based approach in order to find the most sensitive data and prioritise protection efforts around it.
NIST standards are founded on best practices from several security documents, organisations, publications and are designed as a framework for federal agencies and programs requiring strict security measures.
It helps drive our behaviour in a positive way that works for us
& our culture.